| Oracle® Database Enterprise User Administrator's Guide 10g Release 2 (10.2) Part Number B14269-01 |
|
|
PDF · Mobi · ePub |
| Oracle® Database Enterprise User Administrator's Guide 10g Release 2 (10.2) Part Number B14269-01 |
|
|
PDF · Mobi · ePub |
Configuring Enterprise User Security for an Oracle database primarily involves creating directory objects to store enterprise user and database information. For some implementations, it can also require creating special network configuration files (ldap.ora) that enable your databases to locate the correct directory server on the network.
While Enterprise Security Manager is your primary tool for both configuring Enterprise User Security and for administration tasks, this chapter introduces all the available tools, in the following topics:
Enterprise users are database users whose identities are stored and centrally managed in an LDAP directory, such as Oracle Internet Directory. Table 2-1 provides a summary of Enterprise User Security configuration and management tasks and the tools to complete them. The tool names are links to sections that describe them.
Table 2-1 Enterprise User Security Tasks and Tools Summary
| Task | Tools |
|---|---|
| Register and un-register databases in Oracle Internet Directory | Database Configuration Assistant |
|
Enterprise Security Manager and Enterprise Security Manager Console |
| Manage identity management realms in Oracle Internet Directory
For information about this tool and realms, refer to Oracle Identity Management Guide to Delegated Administration. |
Oracle Internet Directory Self-Service Console (Delegated Administration Service) |
| Configure databases Oracle home for directory usage over the network | Oracle Net Configuration Assistant |
| Manage Oracle wallets for Enterprise User Security | Oracle Wallet Manager |
| Perform bulk migrations of database users to Oracle Internet Directory | User Migration Utility |
Database Configuration Assistant is a wizard-based tool used to create and configure Oracle databases.
Use Database Configuration Assistant to register a database with the directory. In that process, Database Configuration Assistant creates a distinguished name (DN) for the database and the corresponding entry and subtree in Oracle Internet Directory.
To start Database Configuration Assistant:
(UNIX) From $ORACLE_HOME/bin, enter dbca at the command line:
(Windows) Choose Start > Programs > Oracle - HOME_NAME > Configuration and Migration Tools > Database Configuration Assistant
See Also:
"To register a database in (or unregister a database from) the directory:" for information about using this tool to register your database
Oracle Database Administrator's Guide for more information about this tool
Security administrators use Oracle Wallet Manager to manage public key security credentials on Oracle clients and servers. The wallets it creates can be read by Oracle Database, Oracle Application Server 10g, and the Oracle Identity Management infrastructure.
See Also:
Oracle Database Advanced Security Administrator's Guide, the wallet manager chapterTo start Oracle Wallet Manager:
(Windows) Select Start, Programs, Oracle-HOME_NAME, Integrated Management Tools, Wallet Manager
(UNIX) At the command line, enter owm.
The orapki command line utility enables administrators to manage wallets, certificate revocation lists, and other public key infrastructure (PKI) elements from the command line. It can be used inside scripts, enabling administrators to automate many routine PKI tasks. The orapki commands enable you to do the following tasks:
Table 2-2 Summary of orapki Commands
| Object Affected | Operations Possible with orapki Commands |
|---|---|
| Certificate | Create or display |
| CRL (certificate revocation list) | Delete, display, hash, list, or upload |
| Wallet | Create, display, add, or export |
See Also:
Full details oforapki commands appear in Appendix E of Oracle Database Advanced Security Administrator's GuideEnterprise User Security employs Enterprise Security Manager and Enterprise Security Manager Console to administer enterprise users, administrative groups, enterprise domains, and enterprise roles stored in Oracle Internet Directory. (Enterprise Security Manager Console can be accessed through the Enterprise Security Manager Operations menu. See "Enterprise Security Manager Console Overview" for details.)
Enterprise users are users provisioned and managed centrally in an LDAP-compliant directory, such as Oracle Internet Directory, for database access. Enterprise domains are directory constructs containing databases, enterprise roles (the access privileges assigned to enterprise users), and proxy permissions (which enable enterprise users to connect to databases as other users).
See Also:
Chapter 1, "Getting Started with Oracle Database Enterprise User Security" for a discussion of Enterprise User Security administrative groups, enterprise domains, enterprise roles, enterprise users, shared schemas, and user-schema mappingsThis section discusses the following topics:
Enterprise Security Manager Initial Installation and Configuration Overview
Navigating Enterprise Security Manager Console User Interface
Enterprise User Security stores enterprise users in Oracle Internet Directory through Enterprise Security Manager, which requires that you first install and configure Oracle Internet Directory and OracleAS Single Sign-On. That installation then supports the services needed for enterprise user administration. Oracle Internet Directory provides the Delegated Administration Services, and OracleAS Single Sign-On authenticates administrators when they log in to the administrative GUI (Enterprise Security Manager Console). Oracle Internet Directory and OracleAS Single Sign-On are part of the Oracle Identity Management infrastructure.
The following elements of Oracle Identity Management infrastructure configuration must be completed before proceeding:
Oracle Internet Directory 10g (9.0.4 or later) must be installed, running, and accessible over standard LDAP or Secure Sockets Layer LDAP (LDAP/SSL).
Oracle Internet Directory must include an identity management realm. You can use Oracle Internet Directory Configuration Assistant to configure this on the directory server.
OracleAS Single Sign-On server must be installed and configured to authenticate enterprise user security administrators when they log in to the Enterprise Security Manager Console, an element of Enterprise Security Manager.
See Also:
Oracle Internet Directory Administrator's Guide for information about using Oracle Internet Directory Configuration Assistant to create or upgrade an identity management realm in the directory. This manual also contains general information about how to configure and use the directory
OracleAS Single Sign-On Administrator's Guide for information about configuring OracleAS Single Sign-On Server
Once these prerequisite tasks are done, you are ready to install Enterprise Security Manager:
Install the Oracle Client.
Choose the Administrator installation type.
See Also:
The Oracle Database installation documentation for your operating systemNote:
Use only the version of Enterprise Security Manager that installs with Oracle Database 10g Release 2 (10.2).To launch Enterprise Security Manager, use the following steps:
Depending on your operating system, use one of the following options:
(UNIX) From $ORACLE_HOME/bin, enter esm at the command line:
(Windows)
Choose Start, Programs, Oracle - HOME_NAME, Integrated Management Tools, Enterprise Security Manager
The directory server login window appears:
To log in to Oracle Internet Directory, supply your full Distinguished Name (DN), select your desired authentication method, and provide the hostname and port number for your directory. Table 2-3 describes the two available Enterprise Security Manager authentication methods and what each method requires:
Table 2-3 Enterprise Security Manager Authentication Methods
| Authentication Method | Description |
|---|---|
| Password Authentication | Uses simple authentication requiring a distinguished name (DN) and passwordFoot 1 . |
| SSL Client Authentication | Uses two-way SSL authentication, in which both the client and server use Oracle Wallets containing digital certificates (that is, the user name and certificate). The subsequent connection is encrypted. |
After providing the directory login information, click OK. The main Enterprise Security Manager user interface appears
The Enterprise Security Manager user interface includes two panes, a toolbar, and various menu items as shown in Figure 2-2.
The navigator pane provides a graphical tree view of your directory's identity management realms and the databases, enterprise domains, and users they contain. You can use the navigator pane to view, modify, add, or delete enterprise domains and the objects they contain.
The navigator pane enables you to
Expand and contract identity management realms by clicking the plus (+) and minus (-) symbols adjacent to the realm name in the navigation tree. This enables you to manage the enterprise domains that they contain.
Right-click an enterprise domain to perform operations such as creating enterprise roles or deleting the domain from the identity management realm.
When you expand an identity management realm, you see a nested list of folders that contain enterprise user security objects. Expanding these folders enables you to view the individual objects as described in Table 2-4.
Table 2-4 Enterprise Security Manager Navigator Pane Folders
| Folder | Description: When you expand this folder, you see: |
|---|---|
| Databases | The list of databases registered with this identity management realm, which was done using Database Configuration Assistant. |
| Enterprise Domains | The enterprise domains that this realm contains. You can also expand each enterprise domain to view the databases and enterprise roles it contains. |
| Users, by Search Base | The users stored in the realm, organized by search base. (User search base is the node in the directory under which a collection of users reside) |
The right pane either displays read-only information about the object selected in the navigator pane, or it displays tabbed windows. These windows enable you to configure enterprise domains, enterprise roles, user-schema mappings, and proxy permissions. For example, when you select an enterprise domain in the navigator pane, you can add databases to it by using the Databases tabbed window shown in Figure 2-3.
Figure 2-3 Enterprise Security Manager Databases Tabbed Window
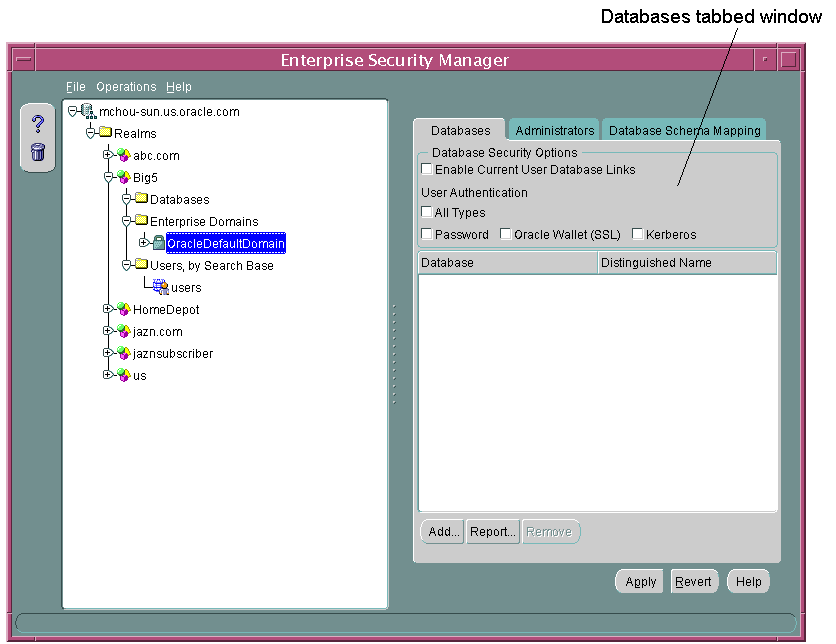
The Databases window also enables you to set security options for databases that are members of an enterprise domain. See "Defining Database Membership of an Enterprise Domain" for a discussion on configuring enterprise domains by using the Databases tabbed window.
The toolbar on the left of the Enterprise Security Manager user interface has two buttons. The buttons allow you to access the Enterprise Security Manager online help and to delete directory objects.
You use Enterprise Security Manager menus to create or remove enterprise domains and to manage objects within the domains, such as enterprise roles, database membership, or proxy permissions. The following sections describe the options available under each menu.
Table 2-5 describes the contents of the File menu.
Table 2-5 Enterprise Security Manager File Menu Options
| Option | Description |
|---|---|
| Change Directory Connection | Causes the Directory Server Login window to reappear (see Figure 2-1), enabling you to log in to another directory server |
| Directory Search Options | Enables you to configure user searches in the directory, setting the maximum number of displayed search results, the maximum search duration, or an LDAP filter |
| ESM Console URL | Enables you to specify the URL for your installation of Enterprise Security Manager Console. (See "Enterprise Security Manager Console Overview") |
| Exit | Exits the Enterprise Security Manager application |
Table 2-6 describes the contents of the Operations menu.
Table 2-6 Enterprise Security Manager Operations Menu Options
| Option | Description |
|---|---|
| Create Enterprise Domain | Creates an enterprise domain in the realm selected in the navigator pane |
| Remove Enterprise Domain | Removes the enterprise domain selected in the navigator pane |
| Create Enterprise Role | Creates an enterprise role in the enterprise domain selected in the navigator pane |
| Remove Enterprise Role | Removes the enterprise role selected in the navigator pane |
| Launch ESM Console | Brings up the Enterprise Security Manager Console in your default browser |
| Create Proxy Permission | Creates a proxy permission in the enterprise domain selected in the navigator pane |
Table 2-7 describes the contents of the Help menu.
Table 2-7 Enterprise Security Manager Help Menu Options
| Option | Description |
|---|---|
| Contents | Opens the online Help and displays its table of contents |
| Search for Help on | Displays the search window for the online help |
| Using Help | Displays online Help topics describing how to use the online Help system |
| About Enterprise Security Manager | Displays Enterprise Security Manager version number and copyright information |
Enterprise Security Manager uses the directory's Enterprise Security Manager Console to administer enterprise users and groups and to configure an identity management realm for Enterprise User Security. By default, when you log in to a directory server with Enterprise Security Manager, it constructs an Enterprise Security Manager Console URL. (This construction uses port 7777 with the fully qualified domain name of that directory server.) Then, when you need to launch the console, Enterprise Security Manager uses this URL to connect to it over HTTP.
For example, suppose an Acme Company administrator logs in to an instance of Oracle Internet Directory hosted on a machine named machine123. Then, Enterprise Security Manager would use the following URL to connect to Enterprise Security Manager Console:
http://machine123.us.acme.com:7777/
After launching the console, an administrator must log in by using his or her OracleAS Single Sign-On user name and password pair.
If you can use the default constructed URL to access an instance of Enterprise Security Manager Console, then use the following steps to log in to the console.
To log in to Enterprise Security Manager Console:
From the Enterprise Security Manager main application window, choose Operations, Launch ESM Console.
The Enterprise Security Manager Console login page appears, as shown in Figure 2-4.
Figure 2-4 Enterprise Security Manager Console Login Page
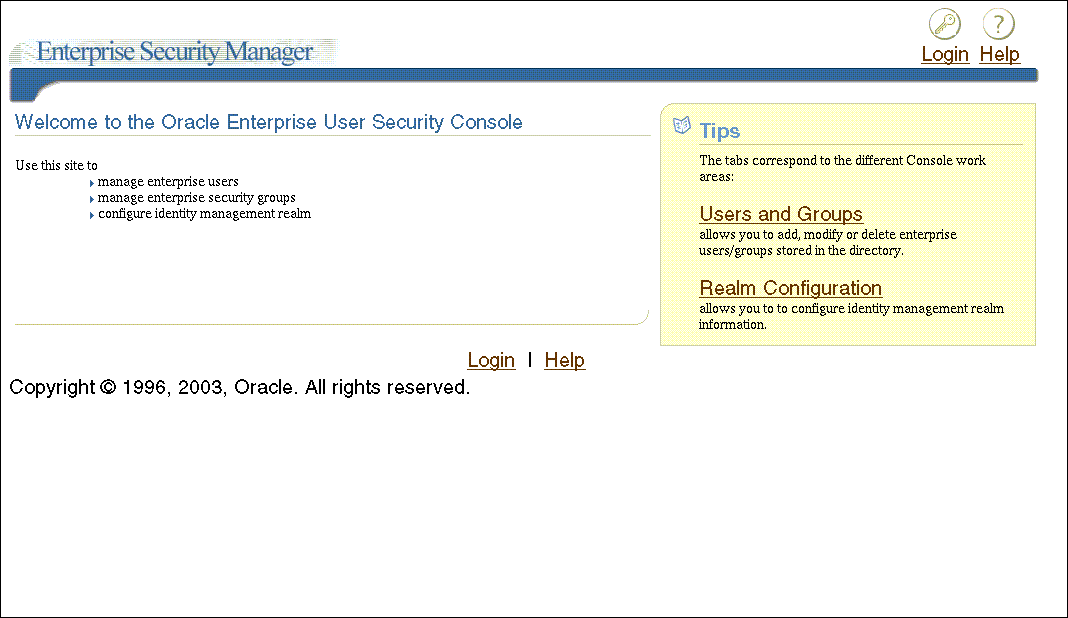
Click the Login icon in the upper right corner of the page to log in with your OracleAS Single Sign-On user name and password.
After providing your OracleAS Single Sign-On credentials, you are returned to the console home page.
To change the default Enterprise Security Manager Console URL:
If you cannot use the default URL to connect to the Enterprise Security Manager Console, then you must enter the appropriate URL before you can launch the console.
In the Enterprise Security Manager main application, choose File, ESM Console URL. The ESM Console URL window appears as shown in Figure 2-5.
Enter the appropriate URL for connecting to Enterprise Security Manager Console, and click OK.
This URL information is saved in Enterprise Security Manager, enabling you to launch the console again without reconfiguring the URL.
By default, Enterprise Security Manager Console user interface does not display the field where you can configure Kerberos principal names. The first time you create Kerberos-authenticated users in the directory, you must configure this tool to display the krbPrincipalName attribute in its Create User window by using the following steps:
Log in to the Oracle Internet Directory Self-Service Console and choose the Configuration tab. See: Oracle Internet Directory Administrator's Guide for information about logging in and using the Oracle Internet Directory Self-Service Console.
In the Configuration page, select the User Entry subtab and click Next until the Configure User Attributes page appears.
In the Configure User Attributes page, click Add New Attribute and the Add New Attribute page appears.
In the Add New Attribute page, select krbPrincipalName from the Directory Attribute Name list (or the attribute that you have configured for orclCommonKrbPrincipalAttribute in your identity management realm) and perform the following steps on this page:
Enter Kerberos Principal Name for the user interface label.
Check Searchable and Viewable.
Select Single Line Text from the UI Type list.
Click Done.
Click Next to navigate to the Configure Attribute Categories page, and click Edit for Basic Information and perform the following steps on this page:
Select krbPrincipalName in the left category list.
Click Move, to move krbPrincipalName to the right-hand list.
Click Done.
Click Next until you reach the last page, and then click Finish to save your work.
The Enterprise Security Manager Console user interface is browser-based and uses tabbed windows instead of a navigator pane. Figure 2-6 shows the layout of the console user interface. The tabbed windows can be accessed by selecting one of the tabs at the top of the application or by selecting one of the links in the Tips box on the right. You can also access the tabbed windows by selecting one of the corresponding links at the bottom of the page.
Figure 2-6 Enterprise Security Manager Console User Interface
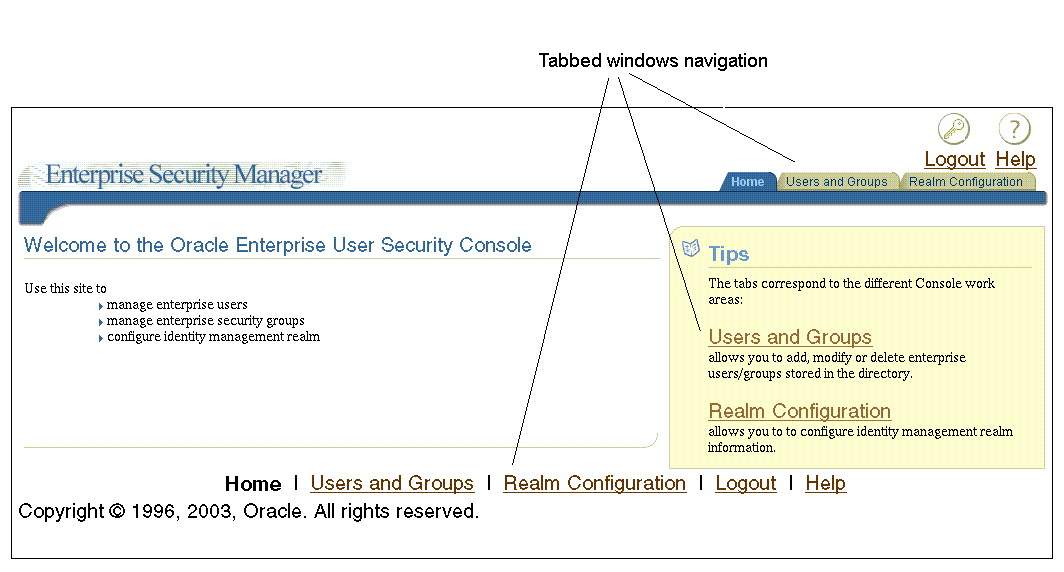
The tabbed windows are explained in the following sections:
The Home page is your entry point to the console. You can access each tabbed window and read a brief summary of what you can do with this tool. The Home tabbed window is shown in Figure 2-6.
This tabbed window contains two subtabs: the Users subtab (shown in Figure 2-7) and the Groups subtab (shown in Figure 2-8).
Figure 2-7 Enterprise Security Manager Console Users Subtab
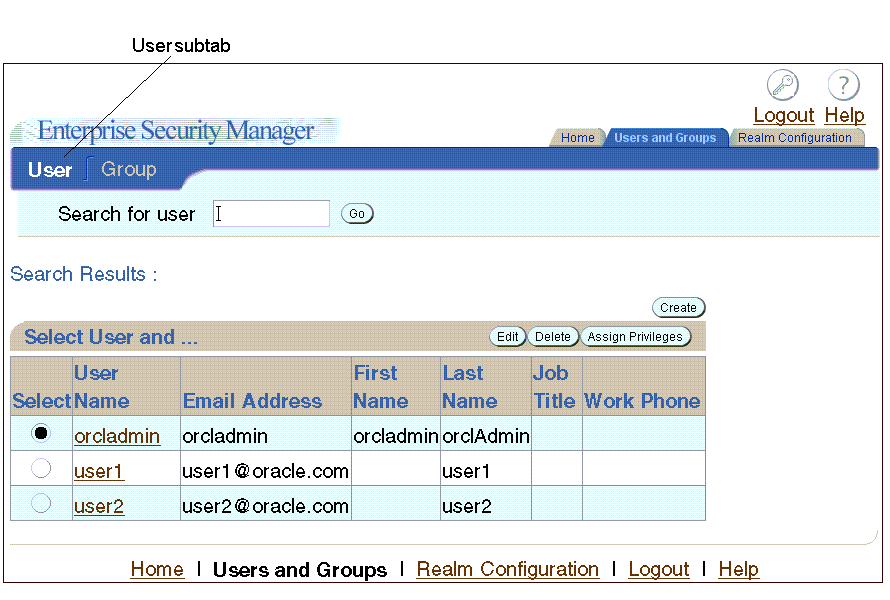
The Users subtab (Figure 2-7) enables you to search for users in the directory by using the Search for user field at the top of the page. After you locate users that match your search criteria, you can select specific users and perform tasks with the buttons listed in Table 2-8. This subtab also enables you to create new users.
Table 2-8 Enterprise Security Manager Console User Subtab Buttons
| Button Name | Description |
|---|---|
| Go | After entering user search criteria in the Search for user field, click Go to display users who match your search criteria in the Search Results table. This button is always available. |
| Create | Enables you to create new enterprise users in the directory. This button is always available. |
| Edit | Enables you to edit a user's information in the directory. This button is available only after you have entered search criteria in the Search for user field and clicked Go. |
| Delete | Enables you to delete a user from the directory. This button is available only after you have entered search criteria in the Search for user field and clicked Go. |
| Assign Privileges | Enables you to assign directory privileges to a specified user. For example, you can assign the privilege to create new users by using this button. This button is available only after you have entered search criteria in the Search for user field and clicked Go. |
The Group subtab (shown in Figure 2-8) enables you to view or to add new users or groups to the Enterprise User Security directory administrative groups. To view or edit an administrative group, select the adjacent option, and click Edit in the upper right corner of the page. When you click Edit, an Edit Group page for the specified group appears, displaying the following information:
Members of the group
Groups of which the specified administrative group is a member
Edit history for the group
You can add members or other groups to a specified Enterprise User Security directory administrative group by clicking either Add User or Add Group in the Member region of the Edit Group page, which is shown in Figure 2-9.
Figure 2-8 Enterprise Security Manager Console Group Subtab
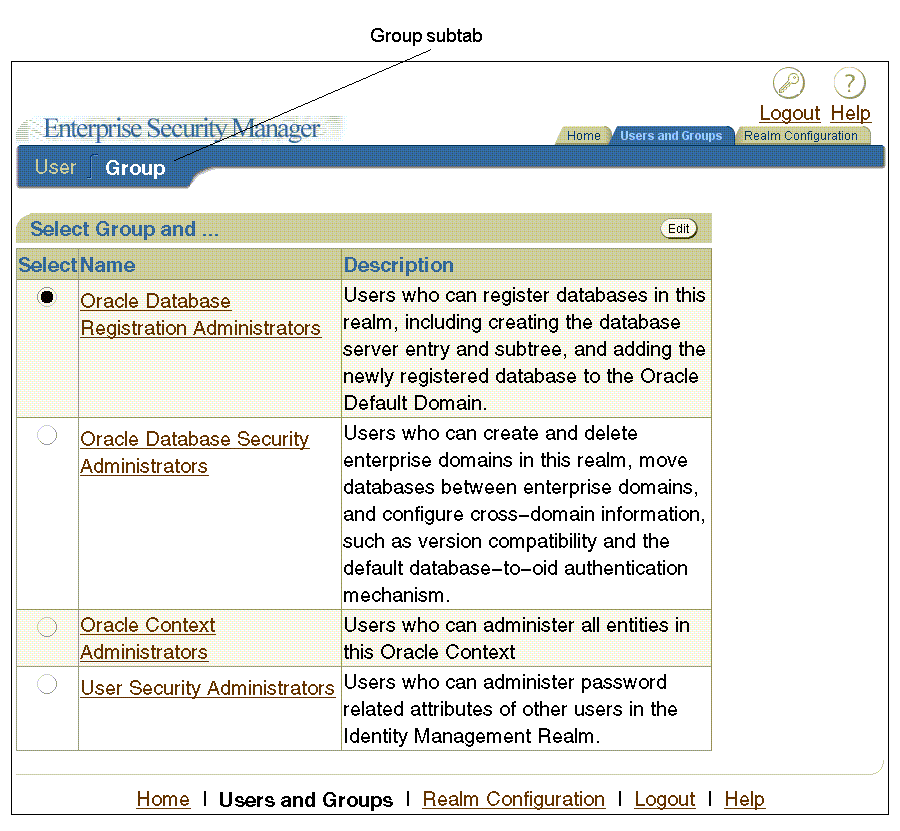
Figure 2-9 Enterprise Security Manager Console Edit Group Page
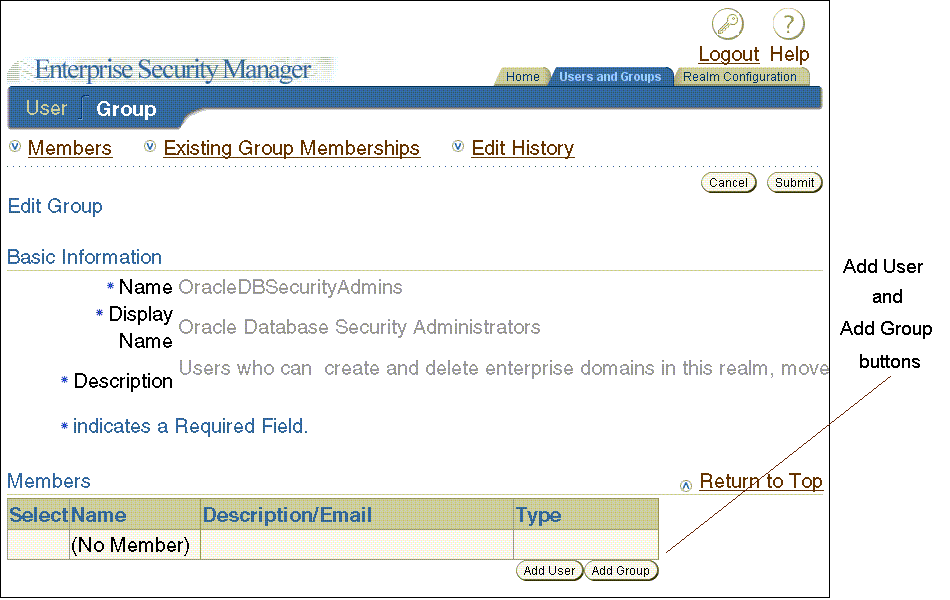
The Realm Configuration tabbed window, which is shown in Figure 2-10, enables you to configure identity management realm attributes that pertain to Enterprise User Security. The fields that you can edit on this page are described in Table 2-9.
Figure 2-10 Enterprise Security Manager Console Realm Configuration Tabbed Window
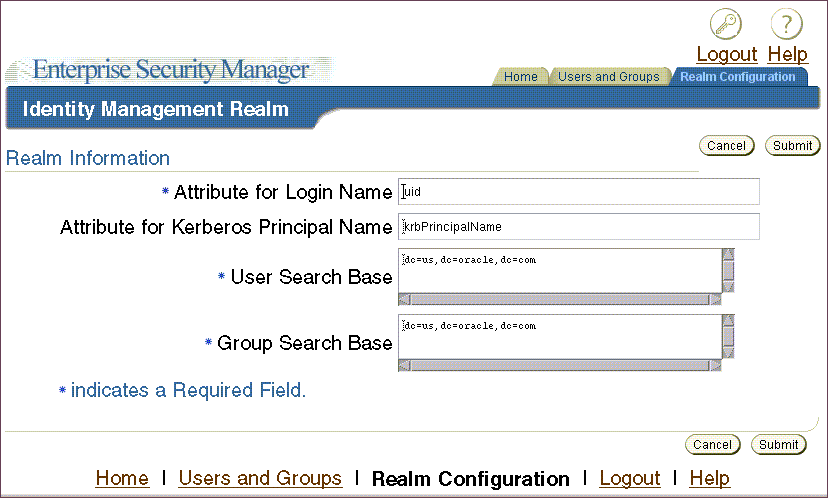
Table 2-9 Realm Configuration Tabbed Window Fields
| Field | Description |
|---|---|
| Attribute for Login Name | Name of the directory attribute used to store login names |
| Attribute for Kerberos Principal Name | Name of the directory attribute used to store Kerberos principal names. See also: "Configuring Enterprise Security Manager Console for Kerberos-Authenticated Enterprise Users" |
| User Search Base | Full distinguished name (DN) for the node under which enterprise users are stored for this realm |
| Group Search Base | Full DN for the node at which user groups (not Enterprise User Security administrative groups) are stored in the directory |
Enterprise Security Manager provides a command-line utility, which can be used to perform the most common tasks that the graphical user interface tool performs. Enter all Enterprise Security Manager command-line utility commands from the Oracle Enterprise Manager Oracle home.
The basic syntax for this utility is as follows:
esm -cmd [operation] [-option_1 -option_2 -option_3 ... -option_n]
For example, the following command searches for users in a directory installed on a host machine named machine1.us.acme.com:
esm -cmd search -U SIMPLE -D orcladmin -w Y4ilbqve -h machine1.us.acme.com
-p 3060 -dn dc=us,dc=acme,dc=com -objectType user
The following table describes each option used in this example:
| Command Option | Description |
|---|---|
-U |
Specifies which authentication type used to log in to the directory. SIMPLE specifies password authentication. |
-D |
Specifies the user name |
-w |
Specifies the password |
-h |
Specifies the directory host machine name |
-p |
Specifies the directory port number |
-dn |
Specifies the search base |
-objectType |
Specifies the type of object for which to search |
To view a full list of operations and options you can use with this utility, enter the following at the command line:
esm -cmd
To view help on a specific operation, enter the following at the command line:
esm -cmd help [operation]
See Also:
"Duties of an Enterprise User Security Administrator/DBA" for a list of tasks that can be performed with Enterprise Security Manager and Enterprise Security Manager Console
Chapter 4, "Administering Enterprise User Security" for detailed information about how to use Enterprise Security Manager and Enterprise Security Manager Console to administer enterprise users
Oracle Net Configuration Assistant is a wizard-based tool with a graphical user interface. Its primary uses are to configure basic Oracle Net network components, such as listener names and protocol addresses, and to configure your Oracle home for directory server usage. The latter use is what makes this tool important for configuring Enterprise User Security.
If you use Domain Name System (DNS) discovery (automatic domain name lookup) to locate Oracle Internet Directory on your network, then this assistant is not necessary. Note that using DNS discovery is the recommended configuration. See Oracle Internet Directory Administrator's Guide for information about this configuration.
Before you can register a database with the directory, you must do either one of the following two tasks:
Configure DNS discovery of Oracle Internet Directory on your network.
See Also:
Oracle Internet Directory Administrator's Guide for information about DNS server discoveryIf DNS discovery is not configured on your network, then use Oracle Net Configuration Assistant to create an ldap.ora file for your Oracle home.
Your database initially uses the ldap.ora file to locate the correct Oracle Internet Directory server on your network. This configuration file contains the hostname, port number, and identity management realm information for your directory server.
Once database registration is complete, the realm is ascertained through the database DN stored in the database wallet.
To start Oracle Net Configuration Assistant:
(UNIX) From $ORACLE_HOME/bin, enter the following at the command line:
netca
(Windows) Choose Start, Programs, Oracle-HOME_NAME, Configuration and Migration Tools, Net Configuration Assistant
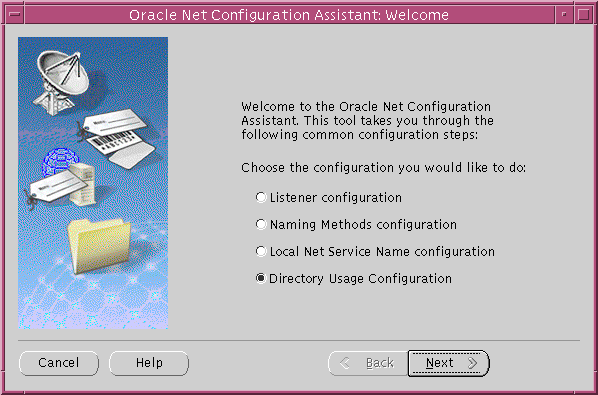
After you start this tool, you will be presented with the opening page shown in Figure 2-11.
Choose the Directory Usage Configuration option on this page, click Next, and choose the directory server where you wish to store your enterprise users. Then, click Finish to create a properly configured ldap.ora file for your Oracle home.
Figure 2-11 Opening Page of Oracle Net Configuration Assistant
See Also:
"Task 5: (Optional) Configure your Oracle home for directory usage" for more information about using this tool to configure your Oracle home for Enterprise User Security
Oracle Net Configuration Assistant online help and Oracle Database Net Services Administrator's Guide for a complete documentation of this tool
User Migration Utility is a command-line tool that enables you to perform bulk migrations of database users to Oracle Internet Directory where they are stored and managed as enterprise users. This tool performs a bulk migration in two phases: In phase one, it populates a table with database user information. During phase two, the database user information is migrated to the directory.
This tool is automatically installed in the following location when you install an Oracle Database client:
$ORACLE_HOME/rdbms/bin/umu
The basic syntax for this utility is as follows:
umu parameter_keyword_1=value1:value2
parameter_keyword_2=value parameter_keyword_3=value1:value2:value3 ... parameter_keyword_n=value
Note that when a parameter takes multiple values, they are separated with colons (:).
See Also:
Appendix A, "Using the User Migration Utility" for complete instructions (including usage examples) for using this tool to migrate database users to a directoryEnterprise User Security administrators plan, implement, and administer enterprise users. Table 2-10 lists the primary tasks of Enterprise User Security administrators, the tools used to perform the tasks, and the links to where the tasks are documented.
Table 2-10 Common Enterprise User Security Administrator Configuration and Administrative Tasks
| Task | Tools Used | See Also |
|---|---|---|
| Create an identity management realm in Oracle Internet Directory | Oracle Internet Directory Self-Service Console (Delegated Administration Service) | Oracle Internet Directory Administrator's Guide for information about how to perform this task |
| Upgrade an identity management realm in Oracle Internet Directory | Oracle Internet Directory Configuration Assistant | Oracle Internet Directory Administrator's Guide and the online Help for this tool |
| Set up DNS to enable automatic discovery of Oracle Internet Directory over the network. Note that this is the recommended configuration. | Oracle Internet Directory Configuration Assistant | Oracle Internet Directory Administrator's Guide (Domain Name System server discovery) and the online Help for this tool |
Create an ldap.ora file to enable directory access |
Oracle Net Configuration Assistant | "Task 5: (Optional) Configure your Oracle home for directory usage" |
| Register a database in the directory | Database Configuration Assistant | "Task 6: Register the database in the directory" |
| Configure password authentication for Enterprise User Security |
|
"Configuring Enterprise User Security for Password Authentication" |
| Configure Kerberos authentication for Enterprise User Security |
|
"Configuring Enterprise User Security for Kerberos Authentication" |
| Configure SSL authentication for Enterprise User Security |
|
"Configuring Enterprise User Security for SSL Authentication" |
| Create or modify user entries and Oracle administrative groups in the directory | Enterprise Security Manager Console | |
| Create or modify enterprise roles and domains in the directory | Enterprise Security Manager | |
| Create or modify wallets for directory, databases, and clients |
|
Oracle Database Advanced Security Administrator's Guide: |
| Change a user's database or directory password | Enterprise Security Manager Console | "Setting Enterprise User Passwords" |
| Change a database's directory password | Database Configuration Assistant | "To change the database's directory password:" |
| Manage user wallets on the local system or update database and directory wallet passwords | Oracle Wallet Manager | Oracle Database Advanced Security Administrator's Guide |
| Request initial Kerberos ticket when KDC is not part of the operating system, such as Kerberos V5 from MIT | okinit utility |
Oracle Database Advanced Security Administrator's Guide for information about using the okinit utility to get an initial Kerberos ticket |
| Migrate large numbers of local or external database users to the directory for Enterprise User Security | User Migration Utility | Appendix A, "Using the User Migration Utility" |