| Oracle® Enterprise Manager Concepts 10g Release 5 (10.2.0.5) Part Number B31949-10 |
|
|
PDF · Mobi · ePub |
| Oracle® Enterprise Manager Concepts 10g Release 5 (10.2.0.5) Part Number B31949-10 |
|
|
PDF · Mobi · ePub |
This chapter describes how you can use Grid Control to manage your Identity Management targets.
This chapter contains the following sections:
Using Grid Control for Monitoring Identity Management Targets
Diagnosing Identity Management Performance and Availability Problems
Access management is the means for controlling user access to enterprise resources. Access management products provide centralized, fine-grained access management for heterogeneous application environments, as well as out-of-the-box integration with Oracle products such as Oracle Portal, Oracle Collaboration Suite, and Oracle E-Business Suite.
Oracle Identity Management is a product set that allows enterprises to manage the end-to-end life cycle of user identities across all enterprise resources both within and beyond the firewall.
Automating user identity provisioning can reduce IT administration costs and improve security. Provisioning also plays an important role in regulatory compliance. Compliance initiatives focus on the enforcement of corporate policies as well as the demonstration of compliance with these standards. An enterprise identity management solution can provide a mechanism for implementing the user management aspects of a corporate policy, as well as a means to audit users and their access privileges.
Oracle Identity management products include the following:
Oracle Access Manager, formerly known as Oracle COREid Access and Identity, provides Web-based identity administration and access control to Web applications and resources running in a heterogeneous environments. It provides the user and group management, delegated administration, password management and self-service functions necessary to manage large user populations in complex, directory-centric environments. Access Manager supports all popular authentication methods including browser forms, digital certificates, and smart cards, and integrates seamlessly with most application servers and portals, including OracleAS 10g, BEA WebLogic, IBM WebSphere, Vignette and others. User identities and credentials can be accessed from a number of repositories including Oracle Internet Directory, Microsoft Active Directory, and Sun Java System Directory. With Access Manager, user access policies can be defined and enforced with a high degree of granularity through centralized management.
The Access Server enables you to protect resources such as URLs and legacy, non-HTTP applications. It provides authentication and authorization services to enterprise applications. It uses the information stored by the Identity Server to control which users, groups, and organizations can access a resource. It stores information about configuration settings and security policies that control access to resources in a directory server that uses Oracle Access Manager-specific object classes. You can use the same directory to store the Access Server configuration settings, access policy data, and user data, or you can store this data on separate directory servers.
The Identity Server is a set of applications that provide delegated administration, user self-service, and real-time change management. The Identity Server stores information about users, groups, and organizations. For example, you can create, manage, and delete groups in the directory server. You can define a subscription policy for a group, including self-service with no approval needed, subscription with approvals, rule-based subscription, and no subscription allowed.
The Oracle Identity Manager platform automates user identity provisioning and deprovisioning and allows enterprises to manage the end-to-end lifecycle of user identities across all enterprise resources, both within and beyond the firewall. It provides an identity management platform that automates user provisioning, identity administration, and password management, wrapped in a comprehensive workflow engine.
Automating user identity provisioning can reduce IT administration costs and improve security. Provisioning also plays an important role in regulatory compliance. Key features of Oracle Identity Manager include password management, workflow and policy management, identity reconciliation, reporting and auditing, and extensibility through adapters.
Oracle Identity Manager also provides attestation support. Attestation is the process of having users or system managers confirm people's access rights on a periodic basis. Existing Sarbanes-Oxley requirements demand enterprises to perform attestation for all financially significant systems every three to six months. Identity Manager includes a highly flexible attestation solution to help enterprise customers meet these regulatory requirements in a cost-effective and timely manner. By setting up attestation processes in Identity Manager, enterprise customers can automate the process of generation, delivery, review, sign-off, delegation, tracking, and archiving of user access rights reports for reviewers on a scheduled or ad-hoc basis.
As more companies move their business processes to the Web, many organizations have a greater need to extend the boundaries of their enterprise to include partner applications. Federated identity management allows companies to operate independently and cooperate for business purposes by enabling cross-domain single sign-on and allowing companies to manage user identities and vouch for them as they access resources managed by another domain.
Oracle Identity Federation, formerly known as COREid Federation, provides a self-contained federation solution that combines the ease of use and portability of a standalone application with a scalable, standards-based proven interoperable architecture. It helps corporations securely link their business partners into a corporate portal or extranet while also increasing their compliance with privacy and security regulations. Identity Federation enables companies to manage multiple partners and choose from industry standard federated protocols. Identity Federation provides built-in integration with customer's identity management infrastructure (Oracle and non-Oracle) to deliver an end-to-end user experience, addressing scenarios like automatic registration, identity mapping, seamless access control navigation, and others.
Enterprise Manager helps you monitor the availability and diagnose the health of Access, Identity, Identity Federation, and Identity Manager servers within your enterprise configuration. By deploying a Management Agent on each host, you can use Enterprise Manager to discover the Identity Management components on these hosts, and automatically begin monitoring them using default monitoring levels, notification rules, and so on.
All Identity Management targets, whether Access, Identity, Identity Federation, and Identity Manager have their own server home pages that provide easy access to key information required by the administrators. Each Identity Management Server home page provides the following information:
Server status, responsiveness, and performance data
Alerts and diagnostic drill-downs so you can identify and resolve problems quickly
Resource usage for the server and its components
Functionality to start, stop, and restart components in the case of locally-monitored Access and Identity servers
Configuration parameters for Access and Identity servers
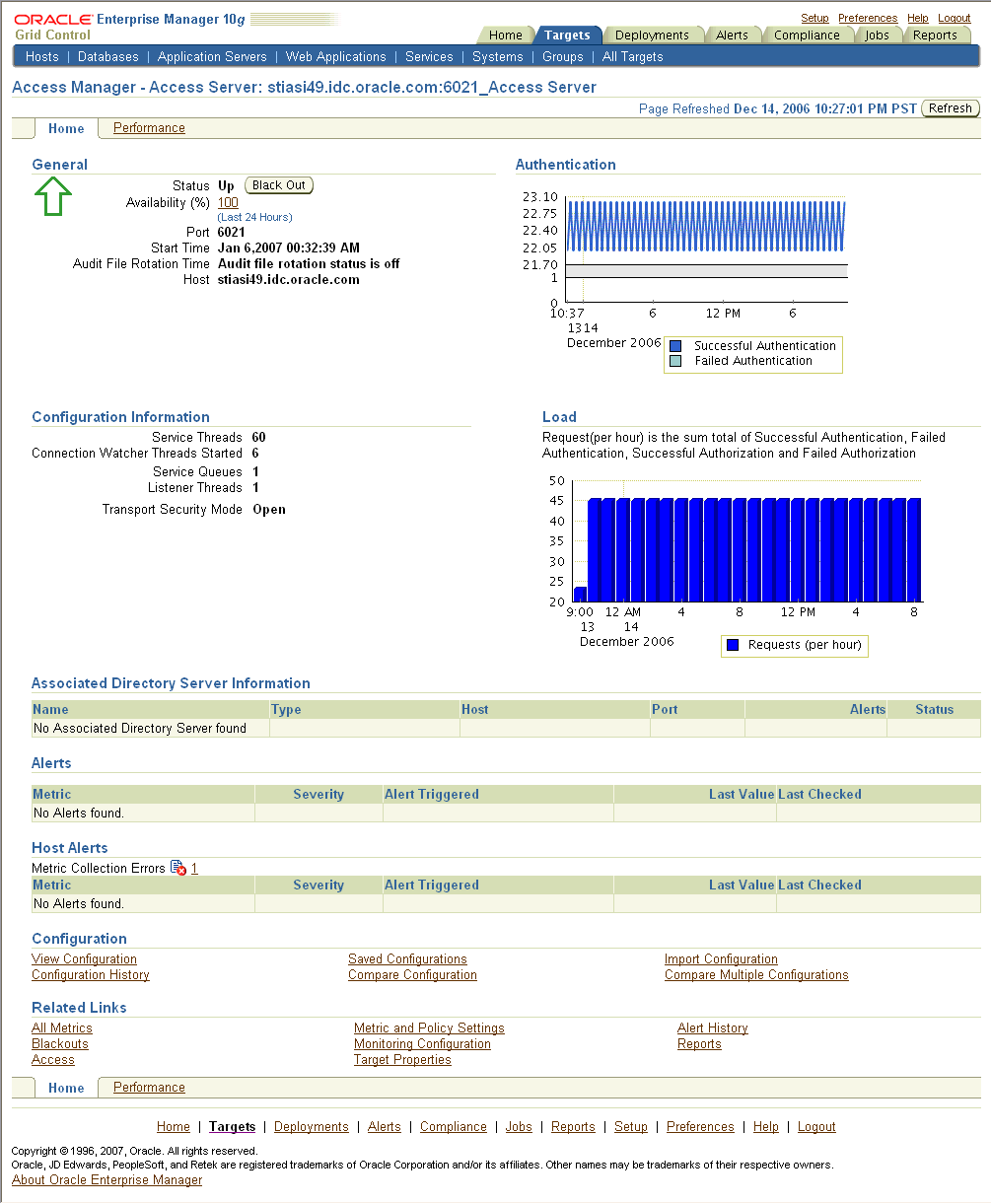
Figure 11-1 shows the Access Manager - Access Server home page.
Figure 11-1 Access Manager - Access Server Home Page
Identity Management services run on Identity Management systems defined in Grid Control. The system includes the software infrastructure components that the Identity services rely on. The system includes components such as databases, HTTP servers, OC4Js, and other servers.
The system is a collection of server targets that are grouped together in Grid Control to give you a view of the "data-center" components that comprise your Identity Management deployment. Identity Management Systems are created when Identity suite components are discovered using Grid Control. Grid Control also monitors the performance and availability of these components and provides a System Dashboard to view the health of the Identity Management system in a single window.
Figure 11-2 shows an Access Manager-Identity System home page:
An Identity Management service is a logical target configured by Grid Control. You use Grid Control to step you through the process of configuring a web application service for your Identity component instances. After you configure a service, that service is displayed on the Services page.
Critical application functions are defined and monitored as services in Grid Control. Each service is monitored by Grid Control beacons, which run service tests that simulate real user access to the service. Service availability and performance are monitored automatically, and problems are immediately reported to the administrator. By monitoring availability and performance of Identity Management services, you can identify and resolve user-visible problems more quickly and thus minimize the impact on users.
Access service allows the Enterprise Manager administrator to perform service-level monitoring. If authentication or authorization services are not available, then the administrator should be notified about the service failures. Administrators will then be able to diagnose the cause of the problem using Root Cause Analysis. For more information about Root Cause Analysis, see "Identity Management Root Cause Analysis".
Discover the Access Server target in Grid Control. For information about discovering this target, see the Grid Control online help. This will create the associated system.
In Grid Control, in the Services tab, select Add Generic Service and click Go.
The Create Generic Service wizard is displayed.
In the Create Generic Service: General page, provide a name for the service and associate the Access system. Click Next.
In the Create Generic Service: Availability page, select Define availability based on Service Test. This allows you to create a web transaction. Click Next.
In the Create Generic Service: Service Test page, provide a name for the web transaction, select Record a Transaction and click Go.
In the Create Service Test page, in the Steps section, click Record.
In the Record Web Transaction page, click Start. A new browser window is displayed.
In the browser, enter the URL that is protected by the Access Server. In the Single Sign-On login page displayed, enter the username and password.
In the Record Web Transaction page, click Stop and then click Continue. The Create Web Applications: Service Test page is displayed again. Click Continue.
In the Create Generic Service: Beacons page, add a beacon to execute the web transaction you created. Click Next.
In the Create Generic Service: Performance Metrics page, click Next.
In the Create Generic Service: Usage Metrics page, click Next.
In the Create Generic Service: Review page, click Finish to create the Access service that will be monitored by the beacon test.
Identity service allows the administrator to perform service-level monitoring of Access Manager Identity. If user management or group management services are not available, then the administrator should be notified about the service failures. Administrators will then be able to diagnose the cause of the problem using Root Cause Analysis. For more information about Root Cause Analysis, see "Identity Management Root Cause Analysis".
Discover the Identity Server target in Grid Control. For information about discovering this target, see the Grid Control online help. This will create the associated system.
In Grid Control, in the Services tab, select Add Generic Service and click Go.
The Create Generic Service wizard is displayed.
In the Create Generic Service: General page, provide a name for the service and associate the Identity system. Click Next.
In the Create Generic Service: Availability page, select Define availability based on Service Test. This allows you to create a web transaction. Click Next.
In the Create Generic Service: Service Test page, provide a name for the web transaction, select Record a Transaction and click Go.
In the Create Service Test page, in the Steps section, click Record.
In the Record Web Transaction page, click Start. A new browser window is displayed.
In the browser, enter the URL of the Identity system (<host:port/identity/oblix>) and then click the Identity System Console link. The login page is displayed.
In the Record Web Transaction page, click Stop and then click Continue. The Create Web Applications: Service Test page is displayed again. Click Continue.
In the Create Generic Service: Beacons page, add a beacon to execute the web transaction you created. Click Next.
In the Create Generic Service: Performance Metrics page, click Next.
In the Create Generic Service: Usage Metrics page, click Next.
In the Create Generic Service: Review page, click Finish to create the Identity service that will be monitored by the beacon test.
Grid Control enables you to monitor all of your Identity Management services. Each service is monitored for performance, usage, and availability.
Each service has its own home page. The Service Home pages in Grid Control provide:
Status, responsiveness, and performance data
Resource usage data for the service
Summary information such as status, performance alerts, usage alerts, and policy violations for the service's subcomponents, including other services and associated systems
Links to home pages for the service's subcomponents
Alerts and diagnostic drill-downs so that you can identify and resolve problems quickly
Services Dashboard
The Services Dashboard provides a high-level view of the status, performance, and usage of each Identity Management target. Service-level compliance for various time periods are also included for each service on the dashboard. You can launch the dashboard directly from Identity system target home page. You can also publish the Services Dashboard so that it can be viewed by non-Enterprise Manager users. This allows you to provide a self-service status web page to your end users.
Related Links to do the following:
View metrics for the service
View client configurations
Edit the service
View the service target's properties
Manage blackouts
View and manage metric thresholds and policies
See Also:
Chapter 6, "Service Management"Individual services in Identity Management are associated with critical system components. This allows Enterprise Manager to perform Root Cause Analysis down to the system level whenever a service outage is detected. When you are configuring an Identity Management service in Grid Control, as mentioned in Configuring Identity Management Services, you also mention the critical system components of this service. When an Identity Management service goes down, Enterprise Manager automatically performs a root cause analysis to determine which critical system component is responsible for this.
Enterprise Manager automatically gathers and evaluates diagnostic information from Identity Management targets distributed across the enterprise. As with all targets managed by Enterprise Manager, an extensive number of Identity Management performance metrics are automatically monitored against predefined thresholds. Alerts are generated in Grid Control when metrics exceed these thresholds.
You can use Grid Control to diagnose performance and availability problems with your Identity Management services. For example, if a service outage occurs, Root Cause Analysis will determine if the primary cause is an outage of a critical service or system component. If a service performance issue is found, an administrator can examine detailed metrics over time related to that service and any of the service or system components used by that service. When you suspect there is a problem with one or more server components in the Identity Management system, the system home pages provide metrics and charts for diagnosing the issue.
Grid Control includes many general features that are useful to an Identity Management administrator, including:
Job Automation: You can use the Grid Control job system to schedule tasks you want to automate.
Policies: You can utilize the policy framework to ensure your Identity Management infrastructure adheres to your site-specific standards.
Database and Application Server Management: Using the single Grid Control console, you can also manage the specific databases and application servers in your Identity Management deployment if needed.
Extensions: Grid Control also includes monitoring of key network components that may be part of your Identity Management deployment. You can also extend Grid Control to monitor other components that are not recognized out-of-box by Enterprise Manager.