| Oracle® Database Advanced Security Administrator's Guide 11g Release 2 (11.2) E40393-03 |
|
|
PDF · Mobi · ePub |
| Oracle® Database Advanced Security Administrator's Guide 11g Release 2 (11.2) E40393-03 |
|
|
PDF · Mobi · ePub |
An Oracle Data Redaction policy defines how to redact data in a column based on the table column type and the type of redaction you want to use. You can enable and disable policies as necessary.
This section contains the following topics:
Redacting Multiple Columns in an Oracle Data Redaction Policy
Restricting Administrative Access to Oracle Data Redaction Policies
To create and manage an Oracle Data Redaction policy, you must have the EXECUTE privilege on the DBMS_REDACT PL/SQL package.
A Data Redaction policy has the following characteristics:
The Data Redaction policy defines the following: What kind of redaction to perform, how the redaction should occur, and when the redaction takes place. Oracle Database performs the redaction at execution time, just before the data is displayed to the application user.
A Data Redaction policy can be defined in such a way as to fully redact the values, partially redact the values, or randomly redact the values. In addition, you can define a Data Redaction policy to not redact any data at all, for when you want to test your policies in a test environment.
A Data Redaction policy can be defined with a policy expression which allows for different application users to be presented with either redacted data or actual data, based on whether the policy expression returns TRUE or FALSE. Redaction takes place when the boolean result of evaluating the policy expression is TRUE. For security reasons, the functions and operators that can be used in the policy expression are limited to SYS_CONTEXT and a few others. User-created functions are not allowed. Policy expressions can make use of the SYS_SESSION_ROLES namespace with the SYS_CONTEXT function to check for enabled roles.
Table 4-1 lists the procedures in the DBMS_REDACT package.
Table 4-1 DBMS_REDACT Procedures
| Procedure | Description |
|---|---|
|
|
Adds a Data Redaction policy to a table or view |
|
|
Modifies a Data Redaction policy |
|
|
Globally updates the full redaction value for a given data type. You must restart the database instance before the updated values can be used. |
|
|
Enables a Data Redaction policy |
|
|
Disables a Data Redaction policy |
|
|
Drops a Data Redaction policy |
See Also:
Oracle Database PL/SQL Packages and Types Reference for detailed information about theDBMS_REDACT PL/SQL packageBefore you create an Oracle Data Redaction policy, it is important to plan the data redaction process that best suits your data.
Ensure that you have been granted the EXECUTE privilege on the DBMS_REDACT PL/SQL package.
Determine the data type of the table column that you want to redact.
Ensure that this column is not used in an Oracle Virtual Private Database (VPD) row filtering condition. That is, it must not be part of the VPD predicate generated by the VPD policy function.
Decide on the type of redaction that you want to perform: full, random, partial, regular expressions, or none.
Decide to whom you want the redacted values to appear.
Based on this information, create the Data Redaction policy by using the DBMS_REDACT.ADD_POLICY procedure.
(Optional) Configure the policy to have additional columns to be redacted, as described in "Redacting Multiple Columns in an Oracle Data Redaction Policy".
After you create the Data Redaction policy, it is automatically enabled and ready to redact data.
To create a Data Redaction policy, use the DBMS_REDACT.ADD_POLICY procedure. The complete syntax is as follows:
DBMS_REDACT.ADD_POLICY ( object_schema IN VARCHAR2 := NULL, object_name IN VARCHAR2 := NULL, policy_name IN VARCHAR2, policy_description IN VARCHAR2 := NULL, column_name IN VARCHAR2 := NULL, column_description IN VARCHAR2 := NULL, function_type IN BINARY_INTEGER := DBMS_REDACT.FULL, function_parameters IN VARCHAR2 := NULL, expression IN VARCHAR2, enable IN BOOLEAN := TRUE, regexp_pattern IN VARCHAR2 := NULL, regexp_replace_string IN VARCHAR2 := NULL, regexp_position IN BINARY_INTEGER :=1, regexp_occurrence IN BINARY_INTEGER :=0, regexp_match_parameter IN VARCHAR2 := NULL);
In this specification:
object_schema: Specifies the schema of the object on which the Data Redaction policy will be applied. If you omit this setting (or enter NULL), then Oracle Database uses the current user's name. Be aware that the meaning of "current user" here can change, depending on where you invoke the DBMS_REDACT.ADD_POLICY procedure.
For example, suppose user mpike grants user fbrown the EXECUTE privilege on a definer's rights PL/SQL package called mpike.protect_data in mpike's schema. From within this package, mpike has coded a procedure called protect_cust_data, which invokes the DBMS_REDACT.ADD_POLICY procedure. User mpike has set the object_schema parameter to NULL.
When fbrown invokes the protect_cust_data procedure in the mpike.protect_data package, Oracle Database attempts to define the Data Redaction policy around the object cust_data in the mpike schema, not the cust_data object in the schema that belongs to fbrown.
object_name: Specifies the name of the table or view to which the Data Redaction policy applies.
policy_name: Specifies the name of the policy to be created. Ensure that this name is unique. You can find a list of existing Data Redaction policies by querying the POLICY_NAME column of the REDACTION_POLICIES data dictionary view.
policy_description: Specifies a brief description of the purpose of the policy.
column_name: Specifies the column whose data you want to redact. Note the following:
You can apply the Data Redaction policy to multiple columns. If you want to apply the Data Redaction policy to multiple columns, then after you use DBMS_REDACT.ADD_POLICY to create the policy, run the DBMS_REDACT.ALTER_POLICY procedure as many times as necessary to add each of the remaining required columns to the policy. See "Altering an Oracle Data Redaction Policy".
Only one policy can be defined on a table or view. You can, however, create a new view on the table, and by defining a second redaction policy on this new view, you can choose to redact the columns in a different way when a query is issued against this new view. When deciding how to redact a given column, Oracle Database uses the policy of the earliest view in a view chain. See "How Oracle Data Redaction Policies Affect Tables and Views" for more information about using Data Redaction policies with views.
If you do not specify a column (for example, by entering NULL), then no columns are redacted by the policy. This enables you to create your policies so that they are in place, and then later on, you can add the column specification when you are ready.
Do not use a column that is currently used in an Oracle Virtual Private Database (VPD) row filtering condition. In other words, the column should not be part of the VPD predicate generated by the VPD policy function. (See "Using Oracle Data Redaction with Oracle Virtual Private Database" for more information about using Data Redaction with VPD.)
You cannot define a Data Redaction policy on a virtual column. In addition, you cannot define a Data Redaction policy on a column that is involved in the SQL expression of any virtual column.
column_description: Specifies a brief description of the column that you are redacting.
function_type: Specifies a function that sets the type of redaction. See the following sections for more information:
If you omit the function_type parameter, then the default redaction function_type setting is DBMS_REDACT.FULL.
function_parameters: Specifies how the column redaction should appear for partial redaction. See "Syntax for Creating a Partial Redaction Policy".
expression: Specifies a Boolean SQL expression. Redaction takes place only if this policy expression evaluates to TRUE. Be careful when making comparisons with NULL. Remember that in SQL the value NULL is undefined, so comparisons with NULL tend to return FALSE. This expression must be based on SYS_CONTEXT values from a specified namespace. The default namespace for SYS_CONTEXT is USERENV, which includes values such as SESSION_USER and CLIENT_IDENTIFIER. (See Oracle Database SQL Language Reference for detailed information about this function.) In addition to SYS_CONTEXT, you can use the V and NV functions (for Oracle Application Express) and the DOMINATES function (for Oracle Label Security). You cannot use user-created functions in the expression parameter.
In the policy expression, in addition to the SYS_CONTEXT function, you can use only the following operators: =, !=, >, <, >=, <=
Another namespace that you can use in a policy expression is the SYS_SESSION_ROLES namespace, which contains attributes for each role. The value of the attribute is TRUE if the specified role is enabled for the querying application user; the value is FALSE if the role is not enabled.
For example, suppose you wanted only supervisors to be allowed to see the actual data. You could use the following expression to have the policy show the actual data to any application user who has the supervisor role enabled, but redact the data for all of the other application users:
expression => 'SYS_CONTEXT(''SYS_SESSION_ROLES'',''SUPERVISOR'') = ''FALSE''',
If you want the Data Redaction policy to always apply, so that redaction always takes place irrespective of the context, then ensure that the Boolean expression evaluates to TRUE, as follows:
expression => '1=1',
Remember that for user SYS and users who have the EXEMPT REDACTION POLICY privilege, all of the Data Redaction policies are bypassed, so the results of their queries are not redacted. See the following sections for more information about users who are exempted from Data Redaction policies:
enable: When set to TRUE, enables the policy upon creation. When set to FALSE, it creates the policy as a disabled policy. The default is TRUE. After you create the policy, you can disable or enable it. See the following sections:
regexp_pattern, regexp_replace_string, regexp_position, regexp_position, regexp_occurrence, regexp_match_parameter: Enable you to use regular expressions to redact data, either fully or partially. If the regexp_pattern does not match anything in the actual data, then full redaction will take place, so be careful when specifying the regexp_pattern. Ensure that all of the values in the column conform to the semantics of the regular expression you are using. See "Syntax for Creating a Regular Expression-Based Redaction Policy" for more information.
This section contains:
A full data redaction policy redacts all the contents of a data column. By default, NUMBER data type columns are replaced with zero (0) and character data type columns are replaced with a single space. You can modify this default by using the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure.
See Also:
"Altering the Default Full Data Redaction Value" if you want to modify the default full redaction valueThe syntax for creating a full data redaction policy is as follows:
DBMS_REDACT.ADD_POLICY (
object_schema IN VARCHAR2 := NULL,
object_name IN VARCHAR2,
column_name IN VARCHAR2 := NULL,
policy_name IN VARCHAR2,
function_type IN BINARY_INTEGER := NULL,
expression IN VARCHAR2,
enable IN BOOLEAN := TRUE);
In this specification:
object_schema, object_name, column_name, policy_name, expression, enable: See "General Syntax of the DBMS_REDACT.ADD_POLICY Procedure".
function_type: Specifies the function used to set the type of redaction. Enter DBMS_REDACT.FULL.
If you omit the function_type parameter, then the default redaction function_type setting is DBMS_REDACT.FULL.
Remember that the data type of the column determines which function_type settings that you are permitted to use. See "Comparison of Full, Partial, and Random Redaction Based on Data Types".
Example 4-1 shows how to use full redaction for all the values in the HR.EMPLOYEES table COMMISSION_PCT column. The expression parameter applies the policy to any user querying the table, except for users who have been granted the EXEMPT REDACTION POLICY system privilege. (See "Exempting Users from Oracle Data Redaction Policies" for more information about the EXEMPT REDACTION POLICY system privilege.)
Example 4-1 Full Data Redaction Policy
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'hr', object_name => 'employees', column_name => 'commission_pct', policy_name => 'redact_com_pct', function_type => DBMS_REDACT.FULL, expression => '1=1'); END; /
Query and redacted result:
SELECT COMMISSION_PCT FROM HR.EMPLOYEES; COMMISSION_PCT ------------ 0 0 0
Example 4-2 shows how to redact fully the user IDs of the user_id column in the mavis.cust_info table. The user_id column is of the VARCHAR2 data type. The output is a blank string. The expression setting enables users who have the MGR role to view the user IDs.
Example 4-2 Fully Redacted Data Redaction Character Values
BEGIN
DBMS_REDACT.ADD_POLICY(
object_schema => 'mavis',
object_name => 'cust_info',
column_name => 'user_id',
policy_name => 'redact_cust_user_ids',
function_type => DBMS_REDACT.FULL,
expression => 'SYS_CONTEXT(''SYS_SESSION_ROLES'',''MGR'') = ''FALSE''');
END;
/
Query and redacted result:
SELECT user_id FROM mavis.cust_info; USER_ID ------------ 0 0 0
This section contains:
Creating Partial Redaction Policies Using Fixed Character Shortcuts
Creating Partial Redaction Policies Using Character Data Types
Creating Partial Redaction Policies Using Date-Time Data Types
In partial data redaction, only a portion of the data, such as the first five digits of an identification number, are redacted. For example, you can redact most of a credit card number with asterisks (*), except for the last 4 digits. You can create policies for columns that use character, number, or date-time data types. For policies that redact character data types, you can use fixed character redaction shortcuts.
The syntax for partial redaction is as follows:
DBMS_REDACT.ADD_POLICY (
object_schema IN VARCHAR2 := NULL,
object_name IN VARCHAR2,
column_name IN VARCHAR2 := NULL,
policy_name IN VARCHAR2,
function_type IN BINARY_INTEGER := NULL,
function_parameters IN VARCHAR2 := NULL,
expression IN VARCHAR2,
enable IN BOOLEAN := TRUE);
In this specification:
object_schema, object_name, column_name, policy_name, expression, enable: See "General Syntax of the DBMS_REDACT.ADD_POLICY Procedure"
function_type: Specifies the function used to set the type of redaction. Enter DBMS_REDACT.PARTIAL.
function_parameters: The parameters that you set here depend on the data type of the column specified for the column_name parameter. See the following sections for details:
The DBMS_REDACT.ADD_POLICY function_parameters parameter enables you to use fixed character shortcuts.
This section contains:
Table 4-2 describes DBMS_REDACT.ADD_POLICY function_parameters parameter shortcuts that you can use for commonly redacted Social Security numbers, postal codes, and credit cards that use either the VARCHAR2 or NUMBER data types for their columns.
Table 4-2 Partial Fixed Character Redaction Shortcuts
| Shortcut | Description |
|---|---|
|
|
Redacts the first 5 numbers of Social Security numbers when the column is a |
|
|
Redacts the last 4 numbers of Social Security numbers when the column is a |
|
|
Redacts the entire Social Security number when the column is a |
|
|
Redacts the first 5 numbers of Social Security numbers when the column is a |
|
|
Redacts the last 4 numbers of Social Security numbers when the column is a |
|
|
Redacts the entire Social Security number when the column is a |
|
|
Redacts a 5-digit postal code when the column is a |
|
|
Redacts a 5-digit postal code when the column is a |
|
|
Redacts dates that are in the |
|
|
Redacts all dates to |
|
|
Redacts a 16-digit credit card number, leaving the last 4 digits displayed. For example, |
See Also:
"General Syntax of the DBMS_REDACT.ADD_POLICY Procedure" for information about otherDBMS_REDACT.ADD_POLICY parametersExample 4-3 shows how Social Security numbers in a VARCHAR2 data type column and can be redacted using the REDACT_US_SSN_F5 shortcut.
Example 4-3 Partially Redacted Data Redaction Character Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'ssn', policy_name => 'redact_cust_ssns3', function_type => DBMS_REDACT.PARTIAL, function_parameters => DBMS_REDACT.REDACT_US_SSN_F5, expression => '1=1', policy_description => 'Partially redacts 1st 5 numbers in SS numbers', column_description => 'ssn contains numeric Social Security numbers'); END; /
Query and redacted result:
SELECT ssn FROM mavis.cust_info; SSN ------- XXX-XX-4320 XXX-XX-4323 XXX-XX-4325 XXX-XX-4329
The DBMS_REDACT.ADD_POLICY function_parameters parameter enables you to redact character data types.
This section contains:
For partial redaction of character data types, for the DBMS_REDACT.ADD_POLICY function_parameters parameter, enter values for the following settings, in the order shown. Separate each value with a comma.
Note:
Be aware that you must use a fixed width character set for the redaction. In other words, each character redacted must be replaced by another of equal byte length. If you want to use a variable-length character set (for example, UTF-8), then you must use a regular expression-based redaction. See "Syntax for Creating a Regular Expression-Based Redaction Policy" for more information.The settings are as follows:
Input format: Defines how the data is currently formatted. Enter V for each character that potentially can be redacted, such as all of the numbers in a credit card number. Enter F for each character that you want to format using a formatting character, such as hyphens or blank spaces in the credit card number. Ensure that each character has a corresponding V or F value. (The input format values are not case-sensitive.)
Output format: Defines how the displayed data should be formatted. Enter V for each character to be potentially redacted. Replace each F character in the input format with the character that you want to use for the displayed output, such as a hyphen. (The output format values are not case-sensitive.)
Mask character: Specifies the character to display for the redaction. Enter a single character to use for the redaction, such as an asterisk (*).
Starting digit position: Specifies the starting V digit position for the redaction.
Ending digit position: Specifies the ending V digit position for the redaction. Do not include the F positions when you decide on the ending position value.
For example, the following setting redacts the first 12 V digits of the credit card number 5105 1051 0510 5100, and replaces the F positions (which are blank spaces) with hyphens to format it in a style normally used for credit card numbers, resulting in ****-****-****-4320.
function_parameters => 'VVVVFVVVVFVVVVFVVVV,VVVV-VVVV-VVVV-VVVV,*,1,12',
See Also:
"General Syntax of the DBMS_REDACT.ADD_POLICY Procedure" for information about otherDBMS_REDACT.ADD_POLICY parametersExample 4-4 shows how to redact Social Security numbers that are in a VARCHAR2 data type column and to preserve the character hyphens in the Social Security number.
Example 4-4 Partially Redacted Data Redaction Character Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'ssn', policy_name => 'redact_cust_ssns2', function_type => DBMS_REDACT.PARTIAL, function_parameters => 'VVVFVVFVVVV,VVV-VV-VVVV,*,1,5', expression => '1=1', policy_description => 'Partially redacts Social Security numbers', column_description => 'ssn contains character Social Security numbers'); END; /
Query and redacted result:
SELECT ssn FROM mavis.cust_info; SSN ----------- ***-**-4320 ***-**-4323 ***-**-4325 ***-**-4329
The DBMS_REDACT.ADD_POLICY function_parameters parameter enables you to redact number data types.
This section contains:
For partial redaction of number data types, enter values for the following settings for the function_parameters parameter of the DBMS_REDACT.ADD_POLICY procedure, in the order shown.
Mask character: Specifies the character to display. Enter a number from 0 to 9.
Starting digit position: Specifies the starting digit position for the redaction, such as 1 for the first digit.
Ending digit position: Specifies the ending digit position for the redaction.
For example, the following setting redacts the first five digits of the Social Security number 987654321, resulting in 999994321.
function_parameters => '9,1,5',
See Also:
"General Syntax of the DBMS_REDACT.ADD_POLICY Procedure" for information about otherDBMS_REDACT.ADD_POLICY parametersExample 4-5 shows how to partially redact a set of Social Security numbers in the mavis.cust_info table, for any application user who logs in. (Hence, the expression parameter evaluates to TRUE.) In this scenario, the Social Security numbers are in a column of the data type NUMBER. In other words, the ssn column contains numbers only, not other characters such as hyphens or blank spaces.
Example 4-5 Partially Redacted Data Redaction Numeric Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'ssn', policy_name => 'redact_cust_ssns1', function_type => DBMS_REDACT.PARTIAL, function_parameters => '7,1,5', expression => '1=1', policy_description => 'Partially redacts Social Security numbers', column_description => 'ssn contains numeric Social Security numbers'); END; /
Query and redacted result:
SELECT ssn FROM mavis.cust_info; SSN --------- 777774320 777774323 777774325 777774329
The DBMS_REDACT.ADD_POLICY function_parameters parameter enables you to redact date-time data types.
This section contains:
For partial redaction of date-time data types, enter values for the following DBMS_REDACT.ADD_POLICY function_parameters parameter settings, in the order shown:
M: Redacts the month. To omit redaction, enter an uppercase M. To redact with a month name, append 1–12 to lowercase m. For example, m5 displays as MAY.
D: Redacts the day of the month. To omit redaction, enter an uppercase D. To redact with a day of the month, append 1–31 to a lowercase d. For example, d7 displays as 07. If you enter a higher number than the days of the month (for example, 31 for the month of February), then the last day of the month is displayed (for example, 28).
Y: Redacts the year. To omit redaction, enter an uppercase Y. To redact with a year, append 1–9999 to a lowercase y. For example, y1984 displays as 84.
H: Redacts the hour. To omit redaction, enter an uppercase H. To redact with an hour, append 0–23 to a lowercase h. For example, h20 displays as 20.
M: Redacts the minute. To omit redaction, enter an uppercase M. To redact with a minute, append 0–59 to a lowercase m. For example, m30 displays as 30.
S: Redacts the second. To omit redaction, enter an uppercase S. To redact with a second, append 0–59 to a lowercase s. For example, s45 displays as 45.
See Also:
"General Syntax of the DBMS_REDACT.ADD_POLICY Procedure" for information about otherDBMS_REDACT.ADD_POLICY parametersExample 4-6 shows how to partially redact a date. This example redacts the birth year of customers; replacing it with 13, but retaining the remaining values.
Example 4-6 Partially Redacted Data Redaction Using Date-Time Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'birth_date', policy_name => 'redact_cust_bdate', function_type => DBMS_REDACT.PARTIAL, function_parameters => 'mDY2013HMS', expression => '1=1', policy_description => 'Replaces birth year with 2013', column_description => 'birth_date contains customer's birthdate'); END; /
Query and redacted result:
SELECT birth_date FROM mavis.cust_info; BIRTH_DATE 07-DEC-13 09.45.40.000000 AM 12-OCT-13 04.23.29.000000 AM
This section contains:
Syntax for Creating a Regular Expression-Based Redaction Policy
Creating Regular Expression-Based Redaction Policies Using Shortcuts
Regular expression-based redaction enables you to search for patterns of data to redact. For example, you can use regular expressions to redact email addresses, which can have varying character lengths. It is designed for use with character data only. You can use shortcuts for the search and replace operation, or you can create custom patterns.
The syntax for regular expression-based data redaction is as follows:
DBMS_REDACT.ADD_POLICY (
object_schema IN VARCHAR2 := NULL,
object_name IN VARCHAR2,
column_name IN VARCHAR2 := NULL,
policy_name IN VARCHAR2,
function_type IN BINARY_INTEGER := NULL,
expression IN VARCHAR2,
enable IN BOOLEAN := TRUE,
regexp_pattern IN VARCHAR2 := NULL,
regexp_replace_string IN VARCHAR2 := NULL,
regexp_position IN BINARY_INTEGER := 1,
regexp_occurrence IN BINARY_INTEGER := 0,
regexp_match_parameter IN VARCHAR2 := NULL);
In this specification:
object_schema, object_name, column_name, policy_name, expression, enable: See "General Syntax of the DBMS_REDACT.ADD_POLICY Procedure".
function_type: Specifies the function used to set the type of redaction. Enter DBMS_REDACT.REGEXP.
Note the following:
When you set the function_type parameter to DBMS_REDACT.REGEXP, omit the function_parameters parameter.
Specify the regular expressions—regexp_pattern, regexp_replace, regexp_position, regexp_occurrence, and regexp_match_parameter—in much the same way that you specify the pattern, replace, position, occurrence, and match_parameter arguments to the REGEXP_REPLACE SQL function. See Oracle Database SQL Language Reference for information about the REGEXP_REPLACE SQL function.
regexp_pattern: Describes the search pattern for data that must be matched. If it finds a match, then Oracle Database replaces the data as specified by the regexp_replace_string setting. See the following sections for more information:
regexp_replace_string: Specifies how you want to replace the data to be redacted. See the following sections for more information:
regexp_position: Specifies the starting position for the string search. The value that you enter must be a positive integer indicating the character of the column_name data where Oracle Database should begin the search. The default is 1 or the RE_BEGINNING shortcut, meaning that Oracle Database begins the search at the first character of the column_name data.
regexp_occurrence: Specifies how to perform the search and replace operation. The value that you enter must be a nonnegative integer indicating the occurrence of the replace operation:
If you specify 0 or the RE_ALL shortcut, then Oracle Database replaces all of the occurrences of the match.
If you specify the RE_FIRST shortcut, then Oracle Database replaces the first occurrence of the match.
If you specify a positive integer n, then Oracle Database replaces the nth occurrence.
If the occurrence is greater than 1, then the database searches for the second occurrence beginning with the first character following the first occurrence of pattern, and so forth.
regexp_match_parameter: Specifies a text literal that lets you change the default matching behavior of the function. The behavior of this parameter is the same for this function as for the REGEXP_REPLACE SQL function. See Oracle Database SQL Language Reference for detailed information.
To filter the search so that it is not case sensitive, specify the RE_MATCH_CASE_INSENSITIVE shortcut.
You can use shortcuts for both the regexp_pattern and regexp_replace_string parameters in the DBMS_REDACT.ADD_POLICY procedure.
This section contains:
Table 4-3 describes the shortcuts that you can use with the regexp_pattern parameter in the DBMS_REDACT.ADD_POLICY procedure.
Table 4-3 Shortcuts for the regexp_pattern Parameter
| Shortcut | Description |
|---|---|
|
|
Matches any digit. The regexp_replace_string => DBMS_REDACT.RE_REDACT_WITH_SINGLE_X, This setting replaces any matched digit with the The following setting replaces any matched digit with the regexp_replace_string => DBMS_REDACT.RE_REDACT_WITH_SINGLE_1, |
|
|
Searches for the middle digits of any credit card that has 6 leading digits and 4 trailing digits with the characters specified by the The appropriate |
|
|
Searches for any U.S. telephone number with the characters specified by the The appropriate |
|
|
Searches for any email address with the characters specified by the The appropriate
|
|
|
Searches for an IP address with the characters specified by the The appropriate |
Table 4-4 describes shortcuts that you can use with the regexp_replace_string parameter in the DBMS_REDACT.ADD_POLICY procedure.
Table 4-4 Shortcuts for the regexp_replace_string Parameter
| Shortcut | Description |
|---|---|
|
|
Replaces the data with a single |
|
|
Replaces the data with a single |
|
|
Redacts the middle digits in credit card numbers, as specified by setting the |
|
|
Redacts the last 7 digits of U.S. telephone numbers, as specified by setting the |
|
|
Redacts the email name as specified by setting the |
|
|
Redacts the email domain as specified by setting the |
|
|
Redacts the last three digits of the IP address as specified by setting the |
Example 4-7 shows how to use regular expression shortcuts to redact credit card numbers.
Example 4-7 Regular Expression Data Redaction Character Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'cc_num', policy_name => 'redact_cust_cc_nums', function_type => DBMS_REDACT.REGEXP, function_parameters => NULL, expression => '1=1', regexp_pattern => DBMS_REDACT.RE_PATTERN_CC_L6_T4, regexp_replace_string => DBMS_REDACT.RE_REDACT_CC_MIDDLE_DIGITS, regexp_position => DBMS_REDACT.RE_BEGINNING, regexp_occurrence => DBMS_REDACT.RE_FIRST, regexp_match_parameter => DBMS_REDACT.RE_MATCH_CASE_INSENSITIVE, policy_description => 'Regular expressions to redact credit card numbers', column_description => 'cc_num contains customer credit card numbers'); END; /
Query and redacted result:
SELECT cc_num FROM mavis.cust_info; CC_NUM ------- 401288XXXXXX1881 411111XXXXXX1111 555555XXXXXX1111 511111XXXXXX1118
You can customize regular expressions in Data Redaction policies.
This section contains:
To create custom regular expression redaction policies, you use the following parameters in the DBMS_REDACT.ADD_POLICY procedure:
regexp_pattern: This pattern is usually a text literal and can be of any of the data types CHAR, VARCHAR2, NCHAR, or NVARCHAR2. The pattern can contain up to 512 bytes. For further information about writing the regular expression for the regexp_pattern parameter, see the description of the pattern argument of the REGEXP_REPLACE SQL function in Oracle Database SQL Language Reference, because the support that Data Redaction provides for regular expression matching is similar to that of the REGEXP_REPLACE SQL function.
regexp_replace_string: This data can be of any of the data types CHAR, VARCHAR2, NCHAR, or NVARCHAR2. The regexp_replace_string can contain up to 500 back references to subexpressions in the form \n, where n is a number from 1 to 9. If you want to include a backslash (\) in the regexp_replace_string setting, then you must precede it with the escape character, which is also a backslash. For example, to literally replace the matched pattern with \2 (rather than replace it with the second matched subexpression of the matched pattern), you enter \\2 in the regexp_replace_string setting. For more information, see Oracle Database SQL Language Reference.
Example 4-8 shows how to use regular expressions to redact the emp_id column data. In this example, taken together, the regexp_pattern and regexp_replace_string parameters do the following: first, find the pattern of 9 digits. For reference, break them into three groups that contain the first 3, the next 2, and then the last 4 digits. Then, replace all 9 digits with XXXXX concatenated with the third group (the last 4 digits) as found in the original pattern.
Example 4-8 Partially Redacted Data Redaction Using Regular Expressions
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'emp_id', policy_name => 'redact_cust_ids', function_type => DBMS_REDACT.REGEXP, expression => '1=1', regexp_pattern => '(\d\d\d)(\d\d)(\d\d\d\d)', regexp_replace_string => 'XXXXX\3', regexp_position => 1, regexp_occurrence => 0, regexp_match_parameter => 'i', policy_description => 'Redacts customer IDs using regular expression', column_description => 'emp_id contains employee ID numbers'); END; /
Query and redacted result:
SELECT emp_id FROM mavis.cust_info; EMP_ID ------------ XXXXX1234 XXXXX5678
This section contains:
A random redaction policy presents the redacted data to the querying application user as randomly generated values each time it is displayed, depending on the data type of the column. Be aware that LOB columns are not supported.
The syntax for creating a random redaction policy is as follows:
DBMS_REDACT.ADD_POLICY (
object_schema IN VARCHAR2 := NULL,
object_name IN VARCHAR2,
column_name IN VARCHAR2 := NULL,
policy_name IN VARCHAR2,
function_type IN BINARY_INTEGER := NULL,
expression IN VARCHAR2,
enable IN BOOLEAN := TRUE);
In this specification:
object_schema, object_name, column_name, policy_name, expression, enable: See "General Syntax of the DBMS_REDACT.ADD_POLICY Procedure".
function_type: Specifies the function used to set the type of redaction. Enter DBMS_REDACT.RANDOM.
If you omit the function_type parameter, then the default redaction function_type setting is DBMS_REDACT.FULL.
Remember that the data type of the column determines which function_type settings that you are permitted to use. See "Comparison of Full, Partial, and Random Redaction Based on Data Types".
Example 4-9 shows how to generate random values. Each time you run the SELECT statement, the output will be different.
Example 4-9 Randomly Redacted Data Redaction Values
BEGIN
DBMS_REDACT.ADD_POLICY(
object_schema => 'mavis',
object_name => 'cust_info',
column_name => 'login_vals',
policy_name => 'redact_cust_rand_vals',
function_type => DBMS_REDACT.RANDOM,
expression => 'SYS_CONTEXT(''USERENV'',''SESSION_USER'') = ''APP_USER''');
END;
/
Query and redacted result:
SELECT login_vals FROM mavis.cust_info;
LOGIN_VALS
----------
N[CG{\pTVcK
This section contains:
The None redaction type option enables you to test the internal operation of your redaction policies, with no effect on the results of queries against tables with policies defined on them. You can use this option to test the redaction policy definitions before applying them to a production environment. Be aware that LOB columns are not supported.
The syntax for create a policy with no redaction is as follows:
DBMS_REDACT.ADD_POLICY (
object_schema IN VARCHAR2 := NULL,
object_name IN VARCHAR2,
column_name IN VARCHAR2 := NULL,
policy_name IN VARCHAR2,
function_type IN BINARY_INTEGER := NULL,
expression IN VARCHAR2,
enable IN BOOLEAN := TRUE);
In this specification:
object_schema, object_name, column_name, policy_name, expression, enable: See "General Syntax of the DBMS_REDACT.ADD_POLICY Procedure".
function_type: Specifies the functions used to set the type of data redaction. Enter DBMS_REDACT.NONE.
If you omit the function_type parameter, then the default redaction function_type setting is DBMS_REDACT.FULL.
Example 4-10 shows how to create a Data Redaction policy that does not redact any of the displayed values.
Example 4-10 No Redacted Data Redaction Values
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'mavis', object_name => 'cust_info', column_name => 'user_name', policy_name => 'redact_cust_no_vals', function_type => DBMS_REDACT.NONE, expression => '1=1'); END; /
Query and redacted result:
SELECT user_name FROM mavis.cust_info; USER_NAME ---------- IDA NEAU
To exempt database users from the Data Redaction policy, grant them the EXEMPT REDACTION POLICY system privilege. Grant this privilege to trusted users only.
In addition to users who were granted this privilege, user SYS is also exempt from all Data Redaction policies. The person who creates the Data Redaction policy is by default not exempt from it, unless this person is user SYS or has the EXEMPT REDACTION POLICY system privilege.
The EXEMPT REDACTION POLICY system privilege is included in the DBA role, but this privilege must be granted explicitly to users because it is not included in the WITH ADMIN OPTION for DBA role grants. For better security, explicitly grant the EXEMPT REDACTION POLICY system privilege to trusted users.
Note the following:
Users who have the INSERT privilege on a table can insert values into a redacted column, regardless of whether a Data Redaction policy exists on the table. Data Redaction only affects SQL SELECT statements (that is, queries) issued by a user, and has no effect on any other SQL issued by a user, including INSERT, UPDATE, or DELETE statements. (See the next bullet for exceptions to this rule.)
Users cannot perform a CREATE TABLE AS SELECT where any of the columns being selected (source columns) is protected by a Data Redaction policy (and similarly, any DML operation where the source is a redacted column), unless the user was granted the EXEMPT REDACTION POLICY system privilege.
Users who were granted the DBA role are exempt from redaction policies because the DBA role contains the EXP_FULL_DATABASE role, which is granted the EXEMPT REDACTION POLICY system privilege.
See Also:
"Oracle Data Pump Security Model for Oracle Data Redaction"for information about how Oracle Data Pump privileges affect theEXEMPT REDACTION POLICY system privilegeYou can use the DBMS_REDACT.ALTER_POLICY procedure to modify Oracle Data Redaction policies. In addition to changing current settings, this procedure enables you to add columns to a policy, if you want to redact more than one column in a database table.
This section contains the following topics:
To alter a Data Redaction policy, use the DBMS_REDACT.ALTER_POLICY procedure. If the policy is already enabled, then you do not need to disable it first, and after you alter the policy, it remains enabled.
You can find the names of existing Data Redaction policies by querying the POLICY_NAME column of the REDACTION_POLICIES data dictionary view, and information about the columns, functions, and parameters specified in a policy by querying the REDACTION_COLUMNS view. To find the current value for policies that use full data redaction, you can query the REDACTION_VALUES_FOR_TYPE_FULL data dictionary view.
The action parameter specifies the type of modification that you want to perform. At a minimum, you must include the object_name and policy_name parameters when you run this procedure.
The syntax for the DBMS_REDACT.ALTER_POLICY procedure is as follows:
DBMS_REDACT.ALTER_POLICY ( object_schema IN VARCHAR2 := NULL, object_name IN VARCHAR2 := NULL, policy_name IN VARCHAR2, action IN BINARY_INTEGER := DBMS_REDACT.ADD_COLUMN, column_name IN VARCHAR2 := NULL, function_type IN BINARY_INTEGER := DBMS_REDACT.FULL, function_parameters IN VARCHAR2 := NULL, expression IN VARCHAR2 := NULL, regexp_pattern IN VARCHAR2 := NULL, regexp_replace_string IN VARCHAR2 := NULL, regexp_position IN BINARY_INTEGER := NULL, regexp_occurrence IN BINARY_INTEGER := NULL, regexp_match_parameter IN VARCHAR2 := NULL, policy_description IN VARCHAR2 := NULL, column_description IN VARCHAR2 := NULL);
In this specification:
action: Enter one of the following values to define the kind of action to use:
DBMS_REDACT.MODIFY_COLUMN if you plan to change the column_name value.
DBMS_REDACT.ADD_COLUMN if you plan to add a new column (in addition to columns that are already protected by the policy) for redaction. This setting is the default for the action parameter.
DBMS_REDACT.DROP_COLUMN if you remove redaction from a column.
DBMS_REDACT.MODIFY_EXPRESSION if you plan to change the expression value. Each policy can have only one policy expression. In other words, when you modify the policy expression, you are replacing the existing policy expression with a new policy expression.
DBMS_REDACT.SET_POLICY_DESCRIPTION if you want to change the description of the policy.
DBMS_REDACT.SET_COLUMN_DESCRIPTION if you want to change the description of the column.
See Also:
"Parameters Required for Various DBMS_REDACT.ALTER_POLICY Actions"
"General Syntax of the DBMS_REDACT.ADD_POLICY Procedure" for information about the remaining parameters
Table 4-5 shows the combinations of parameters that you must use to perform various DBMS_REDACT.ALTER_POLICY actions.
Table 4-5 Parameters Required for Various DBMS_REDACT.ALTER_POLICY Actions
| Desired Alteration | Parameters to Set |
|---|---|
|
Modify a column |
|
|
Add a column |
|
|
Change the policy expression |
|
|
Change the description of the policy |
|
|
Change the description of the column |
|
|
Drop a column |
|
The exercise in this section shows how to modify a Data Redaction policy so that multiple columns are redacted. It also shows how to change the expression setting for the policy. To accomplish this, you must run the DBMS_REDACT.ALTER_POLICY procedure in stages.
Create the policy.
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'hr', object_name => 'employees', column_name => 'email', policy_name => 'hr_employees_pol', function_type => DBMS_REDACT.FULL, expression => '1=1'); END; /
At this point, when application users (including HR) query the email column, the email addresses are redacted to show a single space.
CONNECT HR
Enter password: password
SELECT EMAIL FROM HR.EMPLOYEES;
EMAIL
------
Alter this policy to redact the hire_date column to show 01-JAN-70.
BEGIN DBMS_REDACT.ALTER_POLICY( object_schema => 'hr', object_name => 'employees', policy_name => 'hr_employees_pol', action => DBMS_REDACT.ADD_COLUMN, column_name => 'hire_date', function_type => DBMS_REDACT.PARTIAL, function_parameters => DBMS_REDACT.REDACT_DATE_EPOCH); END; /
To redact the hire_date column, you must change the function_type parameter to use partial redaction, and you must include the function_parameters parameter to specify the DBMS_REDACT.REDACT_DATE_EPOCH shortcut. The expression parameter is omitted because for this particular alteration, it does not need to change. The email column is still redacted, so a query shows the following:
SELECT EMAIL, HIRE_DATE FROM HR.EMPLOYEES;
EMAIL HIRE_DATE
------ ----------
01-JAN-70
Change the expression parameter so that user HR is the only user who can see the actual data for the EMAIL and HIRE_DATE columns.
BEGIN
DBMS_REDACT.ALTER_POLICY(
object_schema => 'hr',
object_name => 'employees',
policy_name => 'hr_employees_pol',
action => DBMS_REDACT.MODIFY_EXPRESSION,
expression => 'SYS_CONTEXT(''USERENV'',''SESSION_USER'') != ''HR''');
END;
/
To change the expression setting, you set the action parameter to DBMS_REDACT.MODIFY_EXPRESSION, and then enter the new expression in the expression parameter. At this stage, when user HR queries the EMAIL and HIRE_DATE columns, he or she can see the actual data.
SELECT EMAIL, HIRE_DATE FROM HR.EMPLOYEES; EMAIL HIRE_DATE ------ ---------- SKING 17-JUN-03 ...
To drop the policy, enter the following procedure.
BEGIN
DBMS_REDACT.DROP_POLICY (
object_schema => 'hr',
object_name => 'employees',
policy_name => 'hr_employees_pol');
END;
/
You can redact more than one column in a Data Redaction policy. To do so, create the policy for the first column that you want to redact. Afterward, use the DBMS_REDACT.ALTER_POLICY procedure to add the next column. As necessary, set the action, column_name, function_type, and function_parameters (or the parameters that begin with regexp_) parameters to define the redaction for the new column, but do not change the object_schema, object_name, policy_name, or expression parameters. The additional columns that you add have no effect on earlier columns that were redacted in the table. In other words, each redacted column continues to have the same redaction parameters that were used to create it.
Example 4-11 shows how to add a column to an existing Data Redaction policy. In this example, the action parameter specifies that a new column must be added, using DBMS_REDACT.ADD_COLUMN. The name of the new column, card_num, is set by the column_name parameter.
Example 4-11 Adding a Column to a Data Redaction Policy
BEGIN
DBMS_REDACT.ALTER_POLICY(
object_schema => 'mavis',
object_name => 'cust_info',
policy_name => 'redact_cust_user_ids',
action => DBMS_REDACT.ADD_COLUMN,
column_name => 'card_num',
function_type => DBMS_REDACT.FULL,
function_parameters => '',
expression => 'SYS_CONTEXT(''SYS_SESSION_ROLES'',''ADM'') = ''TRUE''');
END;
/
You can use the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure to change the default values that are returned for full Data Redaction policies.
This section contains:
Altering the Default Full Data Redaction Value for Non-LOB Data Type Columns
Altering the Default Full Data Redaction Value for LOB Data Type Columns
You can alter the default displayed values for Data Redaction policies that use full data redaction. If you want to change any of the default full redaction values for any of the data types to another value, then you can use the method that applies to that data type, as shown in the following list:
If the data type of the column is a non-LOB data type (BINARY_FLOAT, BINARY_DOUBLE, CHAR, VARCHAR2, NCHAR, NVARCHAR2, DATE, TIMESTAMP, or TIMESTAMP WITH TIME ZONE), then you must use the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure, as described in "Altering the Default Full Data Redaction Value for Non-LOB Data Type Columns".
If the data type of the column is a LOB data type (BLOB, CLOB, or NCLOB), then you must run the UPDATE statement, as described in "Altering the Default Full Data Redaction Value for LOB Data Type Columns".
The modification applies to all of the Data Redaction policies in the current database instance. After you modify a value, you must restart the database for it to take effect. You can find the current values by querying the REDACTION_VALUES_FOR_TYPE_FULL data dictionary view.
To alter the default full data redaction value for non-LOB data type columns, use the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure.
Log in to the database instance as a user who has been granted the EXECUTE privilege on the DBMS_REDACT PL/SQL package.
(Optional) Check the value that you want to change.
For example, to check the current value for columns that use the NUMBER data type:
SELECT NUMBER_VALUE FROM REDACTION_VALUES_FOR_TYPE_FULL;
NUMBER_VALUE
------------
0
Run the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure to modify the value.
Use the following syntax:
EXEC DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES (datatype_value => new_value);
For example, to modify a NUMBER column to use 7 as the default:
EXEC DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES (number_val => 7);
For other data types, replace datatype_value with the following settings, and new_value with the value that you want to use:
| Data Type | new_value Setting | |
|---|---|---|
BINARY_FLOAT |
binfloat_val |
|
BINARY_DOUBLE |
bindouble_val |
|
CHAR |
char_val |
|
VARCHAR2 |
varchar_val |
|
NCHAR |
nchar_val |
|
NVARCHAR2 |
nvarchar_val |
|
DATE |
date_val |
|
TIMESTAMP |
ts_val |
|
TIMESTAMP WITH TIME ZONE |
tswtz_val |
Restart the database instance.
For example:
SHUTDOWN IMMEDIATE STARTUP
See Also:
Oracle Database PL/SQL Packages and Types Reference for more information about the DBMS_REDACT.UPDATE_FULL_REDACTION_VALUES procedure
Oracle Database Reference for more information about the REDACTION_VALUES_FOR_TYPE_FULL view
To alter the default full data redaction value for LOB data type columns:
Log in to the database instance as a user who has privileges to update the RADM_FPTM_LOB$ data dictionary table.
(Optional) Check the value that you want to change by querying the REDACTION_VALUES_FOR_TYPE_FULL data dictionary view.
Update the LOB value.
For the BLOB data type, initialize a variable (for example, blob_val) with the new full Data Redaction value for the BLOB data type. Then run an UPDATE statement on the BLOBVAL column of the RADM_FPTM_LOB$ table to set the new default value for full redaction of columns of the BLOB data type.
DECLARE
blob_val BLOB;
BEGIN
DBMS_LOB.CREATETEMPORARY(blob_val, TRUE);
DBMS_LOB.WRITE(blob_val, 8, 1, UTL_RAW.CAST_TO_RAW('newvalue'));
UPDATE RADM_FPTM_LOB$ SET BLOBCOL = BLOB_VAL WHERE FPVER = 1;
DBMS_LOB.FREETEMPORARY(blob_val);
END;
/
For the CLOB data type, initialize a variable (for example, clob_val) with the new full Data Redaction value for the CLOB data type. Then run an UPDATE statement on the CLOBVAL column of the RADM_FPTM_LOB$ table to set the new default value for full redaction of columns of the CLOB data type.
DECLARE clob_val CLOB; BEGIN DBMS_LOB.CREATETEMPORARY(clob_val, TRUE); DBMS_LOB.WRITE(clob_val, 8, 1, 'newvalue'); UPDATE RADM_FPTM_LOB$ SET CLOBCOL = CLOB_VAL WHERE FPVER = 1; DBMS_LOB.FREETEMPORARY(clob_val); END; /
For the NCLOB data type, initialize a variable (for example, nclob_val) with the new full Data Redaction value for the NCLOB data type. Then run an UPDATE statement on the NCLOBVAL column of the RADM_FPTM_LOB$ table to set the new default value for full redaction of columns of the NCLOB data type.
DECLARE nclob_val NCLOB; BEGIN DBMS_LOB.CREATETEMPORARY(nclob_val, TRUE); DBMS_LOB.WRITE(nclob_val, 8, 1, N'newvalue'); UPDATE RADM_FPTM_LOB$ SET NCLOBCOL = NCLOB_VAL WHERE FPVER = 1; DBMS_LOB.FREETEMPORARY(nclob_val); END; /
Restart the database instance.
For example:
SHUTDOWN IMMEDIATE STARTUP
See Also:
Oracle Database Reference for more information about theREDACTION_VALUES_FOR_TYPE_FULL viewTo disable a Data Redaction policy, use the DBMS_REDACT.DISABLE_POLICY procedure. You can find the names of existing Data Redaction policies and whether they are enabled by querying the POLICY_NAME and ENABLE columns of the REDACTION_POLICIES view. However, as long as the policy still exists, you cannot create another policy for that table or view, even if the original policy is disabled. In other words, if you want to create a different policy on the same table column, then you must drop the first policy before you can create and use the new policy.
DBMS_REDACT.DISABLE_POLICY ( object_schema IN VARCHAR2 DEFAULT NULL, object_name IN VARCHAR2, policy_name IN VARCHAR2);
In this specification:
object_schema: Specifies the schema of the object on which the Data Redaction policy will be applied. If you omit this setting (or enter NULL), then Oracle Database uses the name of the current schema.
object_name: Specifies the name of the table or view to be used for the Data Redaction policy.
policy_name: Specifies the name of the policy to be disabled.
Example 4-12 shows how to disable a Data Redaction policy.
To enable a Data Redaction policy, use the DBMS_REDACT.ENABLE_POLICY procedure. Remember that immediately after you create a new policy, you do not need to enable it; the creation process handles that for you. To find the names of existing Data Redaction policies and whether they are enabled, query the POLICY_NAME and ENABLE columns of the REDACTION_POLICIES view. After you run the procedure, the enablement takes effect immediately.
DBMS_REDACT.ENABLE_POLICY ( object_schema IN VARCHAR2 DEFAULT NULL, object_name IN VARCHAR2, policy_name IN VARCHAR2);
In this specification:
object_schema: Specifies the schema of the object on which the Data Redaction policy will be applied. If you omit this setting (or enter NULL), then Oracle Database uses the name of the current schema.
object_name: Specifies the name of the table or view to be used for the Data Redaction policy.
policy_name: Specifies the name of the policy to be enabled.
Example 4-13 shows how to enable a Data Redaction policy.
To drop a Data Redaction policy, use the DBMS_REDACT.DROP_POLICY procedure. To find the names of existing Data Redaction policies, query the POLICY_NAME column of the REDACTION_POLICIES view. The policy can be either enabled or disabled when you drop it. After you run the procedure, the drop takes effect immediately.
When you drop a table or view that is associated with an Oracle Data Redaction policy, the policy is automatically dropped. As a best practice, drop the policy first, and then drop the table or view afterward. See "Dropping Policies When the Recycle Bin Is Enabled" for more information.
The syntax for dropping a Data Redaction policy is as follows:
DBMS_REDACT.DROP_POLICY ( object_schema IN VARCHAR2 DEFAULT NULL, object_name IN VARCHAR2, policy_name IN VARCHAR2);
In this specification:
object_schema: Specifies the schema of the object to which the Data Redaction policy applies. If you omit this setting (or enter NULL), then Oracle Database uses the name of the current schema.
object_name: Specifies the name of the table or view to be used for the Data Redaction policy.
policy_name: Specifies the name of the policy to be dropped.
Example 4-14 shows how to drop a Data Redaction policy.
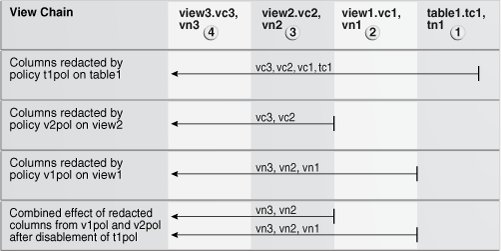
Oracle Data Redaction policies apply to their target table or view and to any views that are created on this target, including materialized views. (See "Creating Policies on Materialized Views" for restrictions on creating Data Redaction policies on materialized views.) If you create a view chain (that is, a view based on another view), then the Data Redaction policy also applies throughout this view chain. The policies remain in effect all of the way up through this view chain, but if another policy is created for one of these views, then for the columns affected in the subsequent views, this new policy takes precedence.
To understand how this concept works:
Create and populate the following table:
CREATE TABLE TABLE1 (TC1 VARCHAR2(20), TN1 NUMBER(10));
INSERT INTO TABLE1 VALUES ('5111-1111-1111-1118', 987654329);
Create the following views, which will constitute the view chain for table table1:
CREATE VIEW view1 (vc1, vn1) AS SELECT tc1, tn1 FROM table1; CREATE VIEW view2 (vc2, vn2) AS SELECT vc1, vn1 FROM view1; CREATE VIEW view3 (vc3, vn3) AS SELECT vc2, vn2 FROM view2;
Create the following policy on the table1 table, which changes the display of the tc1 column to random values.
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'NULL', object_name => 'table1', column_name => 'tc1', policy_name => 't1pol', function_type => DBMS_REDACT.RANDOM, expression => '1=1'); END; /
Query table1.tc1, view1.vc1, view2.vc2, and view3.vc3, and you will see that they all produce random output, based on the t1pol Data Redaction policy.
For example:
SELECT vc3 FROM view3; VC3 ----------------------- M,v]3(z+U4~e;0#3]<'
Create the following policy on view2, which changes the output of column vc2 to display no output at all (that is, a blank space).
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'NULL', object_name => 'view2', column_name => 'vc2', policy_name => 'v2pol', function_type => DBMS_REDACT.FULL, expression => '1=1'); END; /
Query views view2 and view3.
SELECT vc2 FROM view2; SELECT vc3 FROM view3;
Both queries produce the same output (a blank space), which illustrates how for these views, policy v2pol overrides the base table policy, t1pol.
Query table table1 and view view1.
SELECT tc1 FROM table1; SELECT vc1 FROM view1;
Because table1 and view1 are lower in the chain, they are not affected by policy v2pol1. The output for both remains as random values.
Create the following policy on view1, which redacts the first 5 digits of the numeric values in column vn1 to 9.
BEGIN DBMS_REDACT.ADD_POLICY( object_schema => 'NULL', object_name => 'view1', column_name => 'vn1', policy_name => 'v1pol', function_type => DBMS_REDACT.PARTIAL, function_parameters => '9,1,5', expression => '1=1'); END; /
Query view view1:
SELECT vc1, vn1 FROM view1; VC1 VN1 ------------------------------------- ---------------- :'F6`B<dB/N>hJDlJ7V 999994329
Here, view view1 is using two policies. Policy t1pol (on table table1) continues to redact column vc1, and policy v1pol (on view view1) redacts column vn1.
Query view view2:
SELECT vc2, vn2 FROM view2;
VC2 VN2
------------------------------------- ----------------
999994329
View view2 also uses two policies: the blank space for its column vc2 is generated by policy v2pol, and the partial numeric redaction for vn2 comes from policy v1pol for view view1.
Query view view3:
SELECT vc3, vn3 FROM view3;
VC3 VN3
------------------------------------- ----------------
999994329
Because view view3 has no direct policies, it uses the policy settings from both view1 and view2. Hence, the output is the same as the output for view2.
Disable the policy.
If you disable a policy, then the output for all of the views along the view chain that are affected by the policy is also changed.
For example, disable the policy t1pol, which was created for table table1:
EXEC DBMS_REDACT.DISABLE_POLICY (NULL, 'TABLE1', 'T1POL');
Now query view1 again:
SELECT vc1, vn1 FROM view1; VC1 VN1 ------------------------------------- ---------------- 5111-1111-1111-1118 999994329
Column vc1 shows the values from the base table table1. Column vn1 still shows the redacted values from policy v2pol.
To remove the components of this exercise:
EXEC DBMS_REDACT.DROP_POLICY (NULL, 'table1', 't1pol'); EXEC DBMS_REDACT.DROP_POLICY (NULL, 'view1', 'v1pol'); EXEC DBMS_REDACT.DROP_POLICY (NULL, 'view2', 'v2pol'); DROP TABLE table1; DROP VIEW view1; DROP VIEW view2; DROP VIEW view3;
Figure 4-1 shows how these policies affect the chain of views described in the previous example.
Figure 4-1 How Oracle Data Redaction Policies Work in a Chain of Views
See Also:
"Dropping Policies When the Recycle Bin Is Enabled" for information about how Oracle Data Redaction policies are affected when you drop their associated tables or views when the recycle bin is enabledYou can restrict the list of users who can create, view and edit Data Redaction policies by limiting who has the EXECUTE privilege on the DBMS_REDACT package and by limiting who has the SELECT privilege on the REDACTION_POLICIES and REDACTION_COLUMNS views. You also can restrict who is exempted from redaction by limiting the EXEMPT REDACTION POLICY privilege. If you use Oracle Database Vault to restrict privileged user access, then you can use realms to restrict granting of EXEMPT REDACTION POLICY.
See Also:
Oracle Database Vault Administrator's Guide for more information about Oracle Database Vault
Table 4-6 lists data dictionary views that provide information about Data Redaction policies. Before you can query these views, you must be granted the SELECT_CATALOG_ROLE role.
Table 4-6 Data Redaction Views
| View | Description |
|---|---|
|
|
Describes all of the redacted columns in the database, giving the owner of the table or view within which the column resides, the object name, the column name, the type of redaction function, the parameters to the redaction function (if any), and an optional description of the redaction policy |
|
|
Describes all of the data redaction policies in the database. It includes information about the object owner, object name, policy name, policy expression, whether the policy is enabled, and an optional description of the Data Redaction policy. |
|
|
Shows the current redaction values for Data Redaction policies that use full redaction |